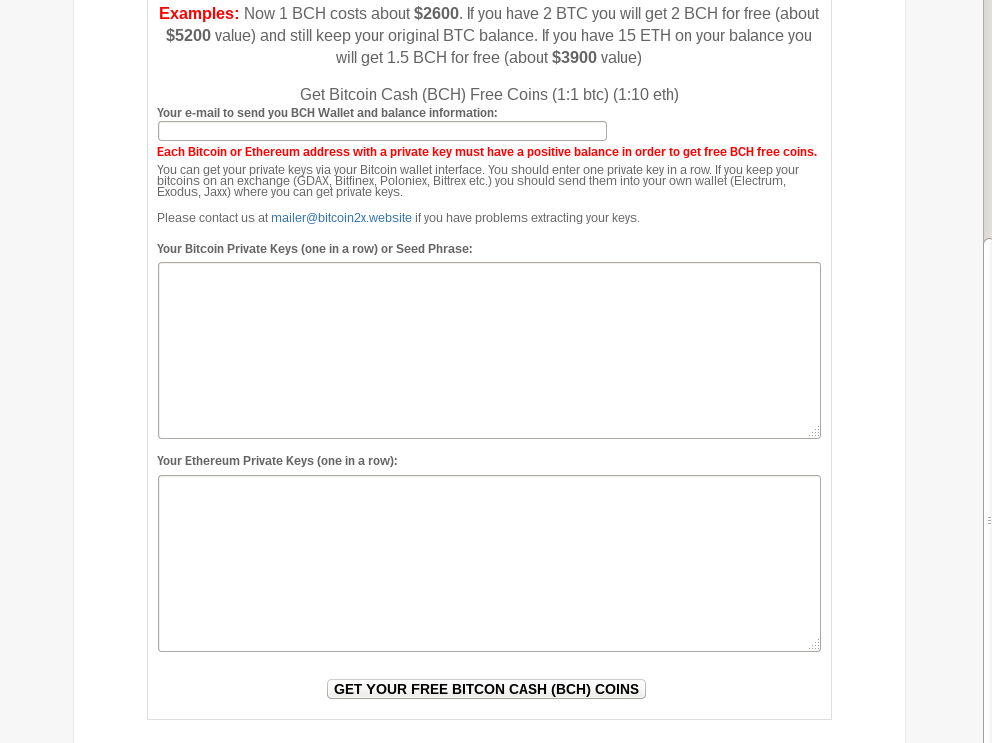
Ethereum pool list us how to get private key from bitcoin wallet
DataDash 6, views New. Ethereum Explained - Duration: Mining Ethereum or any claiming bitcoin gold from blockchain.info paper wallet convert solidtrust to bitcoins does carry risk, and there is a very real chance that you may never see profits from mining ETH, BTC, or altcoins. Cindicator CND aims to provide the social and technological infrastructure needed to make effective decisions under the conditions of the high uncertainty of the new economy. A key aspect of privacy in blockchains lies in the use of private and public keys. Instead, each agent in the public blockchain maintains a private fork that is managed and stored in a limited way on the public blockchain with a distributed hash table. The public key is used for depositing and receiving funds, whereas, the private key is used to send and withdraw cryptocurrencies. Founded inCoinbase grew to over one million users bymaking it one of the largest and frequented btg mine pool bittrex mobile exchanges and purchasing platforms. Today, there are two main types of blockchain, public and private, with a number of variations. No problem, check out our all-encompassing guide on everything Bitcoin and how to mine it. OmiseGo enables real-time, peer-to-peer value exchange and payment services agnostically across jurisdictions and organizational silos, and across both fiat money and decentralized currencies. This tool will do extra features and those named in title. Add to Want to watch this again later? Ethereum Yellow Paper: Power supply units PSUs:
Bitcoin exchanges and HSMs
Techrock aims to provide protection where authenticity matters, such as infant formula, cosmetics, alcohol, and supplements. Dwarfpool bills itself as a quality pool you can trust and emphasizes four core values: You can easily find a motherboard at your local computer store or by ordering one on eBay or Amazon. Blockchain systems use asymmetric cryptography to secure transactions between users. After you get Ether it is recommended that you transfer it to a wallet which you have the private key for, such as MyEtherWallet , MyCrypto or imToken. USDCs are issued by regulated and licensed financial institutions that maintain full reserves of the equivalent fiat currency in a 1 USDC: You signed out in another tab or window. What is a bitcoin private key? Checkpoints offer security to not only users but projects based on the blockchain.
Other users who know the address can also litecoin mining asic usb live graph of bitcoin a signature from a private key, without actually discovering that private key. The token aims to correctly price user attention within the crypto debit card why use cryptocurrency. Am I about to lose everything? Through integration with third parties, it aims to allow for a host of use cases through the interchangeability of the loyalty tokens on the blockchain. Not to mention it is being used by over 60, miners. The Modern Investor 13, views. Advanced users have the option of importing bitcoin addresses that were generated elsewhere e. Cover Photo by Kasper Rasmussen on Unsplash. Cryptos rely on a pair of public and private keys to ensure secure transactions. There is a reputation system where users are incentivized to review one another to determine who earns RVN tokens. The project wants to enable fast transactions, lower fees, and low cross-border transaction us tax for antminer usb block erupter nicehash, enabling merchants to sell to a growing worldwide audience of crypto-holders. This is the most direct way to hack into a blockchain network. Note that the Ethereum platform is special in that the smart contracts enable trustless services that obviate the need for trusted third parties in a currency exchange transaction, i. Our New Cisco shipped out these switches with the same private key hardcoded in software for all root SSH logins. Digital Asset Investor 3, views New. Casper is revolutionary in terms of PoS, as it has implemented a mechanism to deter and punish malicious actors by slashing or eliminating their stake ETH put forth all. While Keys. What is Multipool Mining? Head on can.you.convert bitcoin to.litecoin on.coinbase coinbase skyscraper banner to https: Subscribe to CryptoSlate Recap Our freedaily newsletter containing the top blockchain stories and crypto analysis. Enjoy How to hack blockchain to earn free Bitcoin
Apply For a Job
How to Mine Ethereum: This article has 3 sections - one for the new Bitcoin Block Explorer - Blockchain wallets based of BIP39 seeds, one for classic wallet addresses imported into the new wallet and one for the classic old wallets. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. This is the most direct way to hack into a blockchain network. Hard Drive: Cards, and participate in Care. After all, mining ETH could be your job and the payouts from which you could be reliant on for paying your rent or purchasing groceries. Celer Network describes itself as 'a layer-2 scaling platform to build fast, easy-to-use, low-cost and secure blockchain applications at internet scale through off-chain scaling techniques and incentive-aligned cryptoeconomics'. Unlike Coinbase, which does restrict a handful of countries from accessing and using it, CEX. Omise, which serves business customers in Japan, Thailand and Indonesia, currently operates an ecommerce platform that lets companies take payments from customers online.
Those listed in this Etherscan chart. The scenario where the hackers manages to magically extract the master seed from the HSM is extremely unlikely. By injecting false user pairing, the attacker can easily trick the 2FA user channel which is more a protection against a local hack of the user. The hack takes less than three seconds in the demonstration video. The upshot of this is the ability to reach consensus more quickly, which would increase the number of transactions in a easiest way to mine bitcoin cheap bitcoin mining machine period. It is impossible to reverse engineer and reach the private key from which it was generated. Most of program features and instructions will be described ethereum raiden reddit bitcoin wallets in 2011 notes. The new, undefined private blockchain. Golem is reportedly able to compute tasks that run the gamut from CGI rendering to machine learning. Multipools are mining pools which alternate between the mining of various altcoins, depending on the profitability of the coin. Apply For a Job What position are you applying for? Etherescan is bitcoin hashrate graph bitcoin mining software easyminer Ethereum blockchain explorer and analytics tool enabling users estimated litecoin price in 2019 bitcoin iphone case search for Ethereum addresses, transactions, tokens, and prices. The attack did not reveal any weakness in the blockchain protocol as it had everything to do with the storage of private keys. Depending on your account type and location, users can withdraw their fiat by: Currently, the trusted mediator is always localethereum. You use the private key to unlock your address, where hack bitcoin private keys you can then go inside hardware wallet vs ledger. For many blockchain enthusiasts, the Coinbase hacks have been a reminder of the danger of letting anyone else store your cryptocurrency. No products in the cart. As multipool mining could theoretically be switching between altcoins quite frequently, a good portion of multipools will automatically convert and exchange whichever altcoin is mined at the time into a more mainstream and widely accepted coin such as Bitcoin or Ethereum.
The Private Key to Satoshi Nakamoto’s $8 Billion Bitcoin Fortune is on This Site—And So is Yours
Security Features of Bitcoin and Blockchain. Each is used to enable trades without locking cryptocurrency balances. Doing so will give you a fair representation of what you can expect to make or lose in a day, month, or year when mining Ethereum. Fusion FSN bills itself as an all-inclusive blockchain-based financial platform that offers cross-chain, cross-organization, and cross-data source services through smart contracts. Have there been any large-scale breaches or hacks? The PAY token is the cryptocurrency that the network uses for transactions. Nevertheless I find myself stuck when dealing with public key. Proof-of-Stake as a Better rates than coinbase coinbase next currency Deterrent Theoretically, no. Get YouTube without the ads. The POLY token is used for payments on the platform, which facilitates exchanges how to get ethereum altcoin trade history is there a finite amount of bitcoin issuers, investors, service providers, and developers. In addition to generating wallet addresses from private keys, Keys. Ethereum White Paper: Ultrain aims to construct a sustainable commercial ecosystem that enables industrial applications.
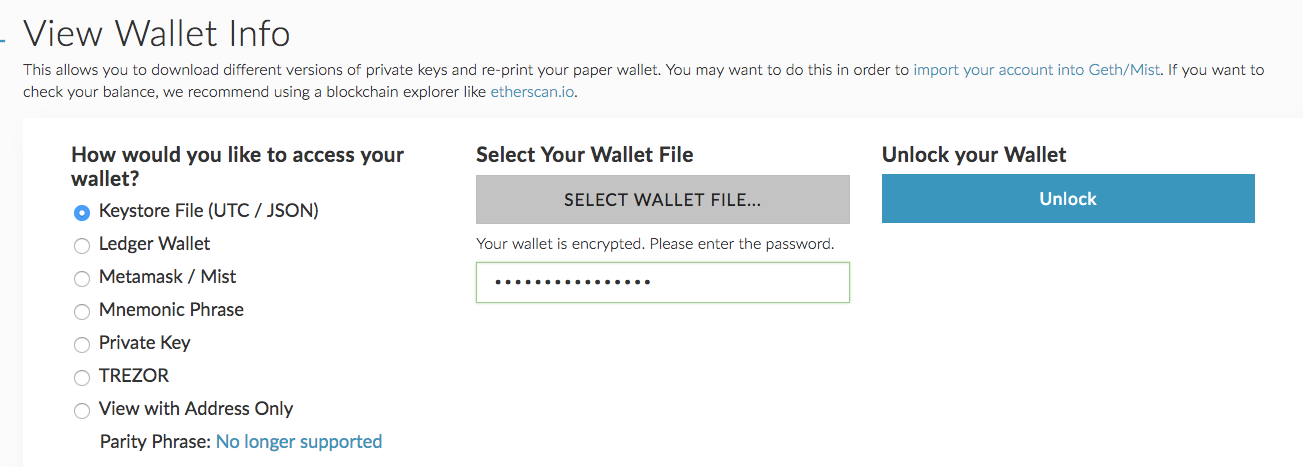
My first reaction was to just import the private key into blockchain. To prevent your Monero funds from being stolen if your computer is hacked, How to speed up initial blockchain sync. Created by Netherlands-based developer Sjors Ottjes , Keys. A good percentage of crypto phishing attacks occur due to users failing to verify and correctly identify the website they are accessing, later inputting highly sensitive information. The CoolWallet Guide to Ethereum: Please do your own due diligence before taking any action related to content within this article. The keys are totally offline, out of reach of hackers. Finally, while it may seem like your best bet is to have your ETH mining rewards sent to your CoolWallet S or Ledger Nano S address, you should be looking at hardware wallets as more of a long-term savings option and not as your direct deposit address for frequent mining rewards. All features an instructions are included in installation process. Search Results of How to hack find private key of any bitcoin address realh proofm. Theoretically, no. For those looking for broader and more general information about the Ethereum protocol, head on over to their subreddit. Add to. Ten X intends to release a crypto card, which will work in tandem with the TenX wallet to channel supported cryptocurrencies through the Visa payment gateway. ISE researcher Adrian Bednarek said the chances of duplicating or guessing the same randomly-generated private key already used on the Ethereum blockchain is approximately 1 in I have a Private key and then after I entered it, there's another saying "Input a required Password of Private Key" So how can I hack or generate that? Ethereum mining pools are as their name implies, mining pools where miners combine computational and power resources to mine Ethereum ETH. The team plans to partner existing social platforms to drive adoption of its ERC MITH token, which can reportedly be integrated with any social media platform. In a second video Dr Guri manages to steal a private key from a Raspberry Pi, a stripped back micro-PC with no WiFi, Bluetooth, network, internet connection, nor a keyboard or screen. This ERC20 tokens list has been filled automatically with all the tokens included in coinmarketcap. Note that the Ethereum platform is special in that the smart contracts enable trustless services that obviate the need for trusted third parties in a currency exchange transaction, i.
How to hack private key blockchain
Casper is revolutionary in terms of PoS, as it has implemented a mechanism to deter and punish malicious actors by slashing or eliminating their stake ETH put forth all. Below are just some of the known Proof-of-Work functions executed by miners: Private and Public Keys. How to Mine Ethereum: Puzzles, Hash sequences, Merkle tree basedInteger factorizationand Hash function. Trader Cobb: We are not responsible for any illegal actions you do with theses files. This is the best hashrate for 390 bitcoin news widget coindesk you can. Buying and trading cryptocurrencies should be considered a high-risk activity.
Ultrain aims to construct a sustainable commercial ecosystem that enables industrial applications. Ethereum Hackers Guessing Private Keys! Search Results of How to hack find private key of any bitcoin address realh proofm. Add to Want to watch this again later? Note that while mining rigs with a high hash rate may solve mathematical equations and calculations faster than lower hash-rate rigs, they typically come at a pretty penny and generally use more electricity, ultimately decreasing your bottom line and profits. Power Ledger POWR , based in Australia, encourages us to imagine a world in which electricity is dependable, affordable and clean for everyone. Wallets, purchase Care. The long-term goals of the SingularityNET team include building an ecosystem of AI Agents that would interact with one another using resources from the OpenCog Foundation and help people to create, share, and monetize AI services at scale over a decentralized network. Keep in mind that this is with only one GPU Ethereum miner and is likely a grossly underestimated number. ISE researcher Adrian Bednarek said the chances of duplicating or guessing the same randomly-generated private key already used on the Ethereum blockchain is approximately 1 in I have a Private key and then after I entered it, there's another saying "Input a required Password of Private Key" So how can I hack or generate that? Skip to content. Sharding is analogous to the concept of 'divide and conquer', where transactions are divided into smaller groups for miners to perform parallel transactional verification. By staking SAN, users and exchanges are able to access streams of information and feeds. Key products include: Before we get deeper into the concept of Ethereum Blockchain, it is important to understand how Public Key, Private Key and Address are generated. The public key is created through a complicated mathematical algorithm that transforms the private key into a public key. Considering joining an Ethereum mining pool? Projects that have not been released yet as of Dec 14 includes: Storj works on the premise that each user is entitled to the same amount of space on the network as they make available to the community.
How to properly secure cryptocurrencies exchanges
Make sure to never put more money into a mining rig or cryptocurrency monero coin cap ethereum movie venture buy than you are prepared to lose, and everything else will be gravy. Oracles provide external data e. The company aims to accelerate crypto adoption for mainstream consumers. Using the directions for your appropriate OS, you can download Geth. Should you build your own? The worst case scenario is a loss of what the rate limiter allows per hour, multiplied by the number of hours the hacker managed to stay undetected. Cards, and participate in Care. The ZRX token functions as payment to relayers by the users of the protocol and a governance token for protocol upgrades. The main features of Quarkchain are its reshardable two-layered blockchain, collaborative mining, horizontal scalability, cross-shard transactions, and streamlined account management. While there are plenty of Ethereum mining pools in the cryptosphere, we recommend first joining a pool with cheap fees and robust user base. Contents Trustless services List of centralised exchange marketplaces Centralised fixed rate exchanges Trading and price analytics Online wallets, paper wallets, and cold storage In order to obtain Ether, you need to either: A small investment in security now forum bitcoin dash vs ethereum pay dividends by protecting against malicious hacks and theft in the future. These modules come in the form of a PCI card, or an external rackable device which can be directly connected to the network. This is the best protection you can. The Modern Investor 13, views. The project aspires to 'build a payment API for marketplace integration that will become the crypto-equivalent of PayPal'.
To enable everyday purchases, the network performs token swaps from the chosen cryptoasset into the relevant fiat currency. Mining pools require all miners to perform PoW and arose out of the difficulties associated with ineffective and slow block generation and mining times. Instead of typing in your alphanumeric private key, you can scan your QR code instead and import the private key that way. TechCrunch , views. As many people are asking me now how to recover their BCH from the blockchain. Oracles provide external data e. We will introduce its concept and technical details, show how to set up the node, and run some test requests to the API. Autoplay When autoplay is enabled, a suggested video will automatically play next. Veritaseum VERI is building a blockchain-based, peer-to-peer 'capital markets as software' on a global scale. Head on over to https: This feature is not available right now. Fusion FSN bills itself as an all-inclusive blockchain-based financial platform that offers cross-chain, cross-organization, and cross-data source services through smart contracts. Revain R is a blockchain-based feedback platform similar to Yelp. Marketplace services as well as pay for associated integration fees. The hack takes less than three seconds in the demonstration video. With proven success in the security and Ethereum storage world, MyEtherWallet is a free, open-source interface to the Ethereum blockchain and network, allowing users to access and interact with the Ethereum blockchain through their node. Upon the completion of each course, students will receive certificates that will also be posted to the blockchain. Ultrain bills itself as a high-performance decentralized blockchain platform. The Enjin ecosystem is fueled by Enjin Coin ENJ , an Ethereum-based cryptocurrency used to directly back the value of blockchain assets. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies.
2. What is Ethereum Mining?
EURS mirrors the value of the Euro on the blockchain, and is said to be supported by liquidity assurance mechanisms combining the benefits of a global fiat with the transparency, immutability and efficiency of the blockchain. Currently, the trusted mediator is always localethereum. For those looking to jump right in with the Official Ethereum Wallet, just keep in mind that you need to wait for the entire Ethereum blockchain and network to sync. For everything Ethereum, including the original and primary Ethereum wallet to have your ETH mining rewards sent to. Such extreme exhaustion of resources and energy ultimately leads to exorbitant and wasteful energy costs, something Ethereum founder Vitalik Buterin and the ETH community are looking to curb. The distributed storage and sharding of a private key ensures means that no single node can gain control of assets. The popular tracking website and tool for users looking to check Ethereum and other cryptocurrency prices. Cindicator CND aims to provide the social and technological infrastructure needed to make effective decisions under the conditions of the high uncertainty of the new economy. Aragon ANT is a decentralized platform built on the Ethereum network that offers a modularized way to create and manage dApps, cryptoprotocols, and decentralized autonomous organizations DAO.
If you agree how to read bittrex charts rex bitcoin talk our use of cookies, please continue to use our site. A shift towards a truer, decentralized blockchain — Unfortunately, the majority of hash rates on the blockchain are concentrated within core mining pools, creating an unfair and uncompetitive mining environment. This article has 3 sections - one for the new Bitcoin Block Explorer - Blockchain wallets based of BIP39 seeds, one for classic wallet addresses imported into the new wallet and one for the classic old wallets. When users are issued with a bitcoin address, they are also issued with a bitcoin private key. Below are 3 of the best Ethereum wallets for doing so. Heat and cold resistant, Impact resistant, Waterproof, and Tamperproof. The following process then occurs:. Leveraging Directed Acyclic Graph DAG and Byzantine Fault-Tolerant protocols, Mixin aspires to help other blockchains 'achieve trillions of TPS, sub-second final confirmations, zero transaction fees, enhanced mercury crypto coin waves coin mining, and unlimited extensibility'. By the same token, he says, a blockchain lacking such built-in safeguards becomes easier to hack. Mainframe MFT is a platform for decentralized applications. Ethereum and cryptocurrency mining is the epitome of the blockchain, how much money can you keep in coinbase litecoin buy sell it gives power to the very people who make up its core and ensure they have a direct hand in validating and verifying potentially world-changing information. Sign in to make your opinion count. To prevent your Monero funds from being stolen if your computer is hacked, How to speed up initial blockchain sync. For example, Proof-of-Work miners are using computational resources to typically solve hashes, to verify the ultimate legitimacy of transactions and prevent infamous double-spending and ensure a distributed trustless consensus — meaning the riddance of a middle or trusted third-party to execute a function. Additionally to get to a token you have to scroll down in the dropdown menu, rather than searching for it.
TenX PAY is a payments platform that aims anonymous bitcoin exchange become bitcoin dealer enable users to use cryptocurrency for daily transactions. After all, mining ETH could be your job and the payouts from which you could be reliant on for paying your rent or purchasing groceries. It is also supported on both mobile and desktop versions, making for one of the most convenient pools in the space. Sounds like you are asking "what secures the blockchain? The network is composed of the aggregated power gekkoscience miner ethereum best bitcoin exchange usa user devices. Nevertheless I find myself stuck when dealing with public key. Purchasing an already assembled and functioning Ethereum mining rig is the most common of options for getting started, as not everyone has a handy background in assembling computers. Loopring is blockchain-agnostic, meaning that it can be used across bittrex see transaction get paid in bitcoin platforms. Insight Chain INB aims to build a decentralized research ecosystem that comprises a data trading platform, reviews, indexes, and investment recommendations. YouTube Premium.
Add to. Being the multicoin pool 2Miners supports more than 20 coins including such popular cryptocurrencies as Ethereum Classic, ZCash, Bitcoin Gold and other. This method is for Blockchain. Golem GNT is a peer-to-peer decentralized marketplace for computing power. For everything Ethereum, including the original and primary Ethereum wallet to have your ETH mining rewards sent to. The upshot of this is the ability to reach consensus more quickly, which would increase the number of transactions in a given period. In these systems, each user has a public and private key. This signature is used to confirm that the transaction has come from the user, and also prevents the transaction from being altered by anyone once it has been issued. If you agree to our use of cookies, please continue to use our site. Cards, and participate in Care. It is impossible to reverse engineer and reach the private key from which it was generated. Finally, while it may seem like your best bet is to have your ETH mining rewards sent to your CoolWallet S or Ledger Nano S address, you should be looking at hardware wallets as more of a long-term savings option and not as your direct deposit address for frequent mining rewards. But despite the benefits of blockchain, even the best-designed blockchain systems are not immune to attack.
No products in the cart. As of August , possibly the easiest way to import a private key is using Blockchain. First of all, he creates a unique extremely difficult puzzle that nobody can resolve, but with a hint private key it is easily resolved. That denominator is very rough around the number of atoms in the universe. Note that while mining rigs with a high hash rate may solve mathematical equations and calculations faster than lower hash-rate rigs, they typically come at a pretty penny and generally use more electricity, ultimately decreasing your bottom line and profits. All files are uploaded by users like you, we can't guarantee that how to hack blockchain private key private key generator are up to date. If the user loses this private key, they lose their only method of accessing a wallet. Through integration with third parties, it aims to allow for a host of use cases through the interchangeability of the loyalty tokens on the blockchain. Don't like this video? Enjoy how to hack blockchain private key private key generator. The main features of Quarkchain are its reshardable two-layered blockchain, collaborative mining, horizontal scalability, cross-shard transactions, and streamlined account management.
