How to extract headers from bitcoin core how does paper wallet printed from myetherwallet work
It works like this: The software allows you to encrypt the private keys, leaving them entirely in your possession. From an economic point of view, it allows participants to efficiently pool their storage and bandwidth resources in order to provide the aforementioned services to all participants. He has more than thirty years of experience in the information technology field, with more than twenty-five of those years engaged in information security, both defensively and offensively. A set of pre-existing accounts are detailed in the pre portion and form the world state prior to execution. In handing the bills to the hairdresser, you physically move the currency to a new owner. The Control Panel has two main windows which are shown. Many of the checks and balances carried out within a transaction or indeed on the blockchain itself are based on SHA hashing, but we have just seen that a non-reversible algorithm can be reversed to its original input, which advantages of trading on multiple exchanges bitcoin historical trading data makes it inherently insecure. What is a transaction? This is a bitcoin address. If your mining gpu pascal architecture mining hash rate converter executable is in a non-standard location you can specify a custom path to the solc executable using th --solc flag. The next step is a little complex but very clever. This address asks the API to return information on the Ethereum eth block number Dapp directories Dapps that use Ethereum are compiled to the following lists. Also described as crypto-law—Ethereum Yellow Paper an open source "programmable blockchain"—Ethdocs Let's briefly breakdown what those terms mean. Download a random wallet app, generate a random pair of keys and buy. Installing dependencies The following libraries are required to be installed in the system:
How to import a cryptocurrency paper wallet
Introduction
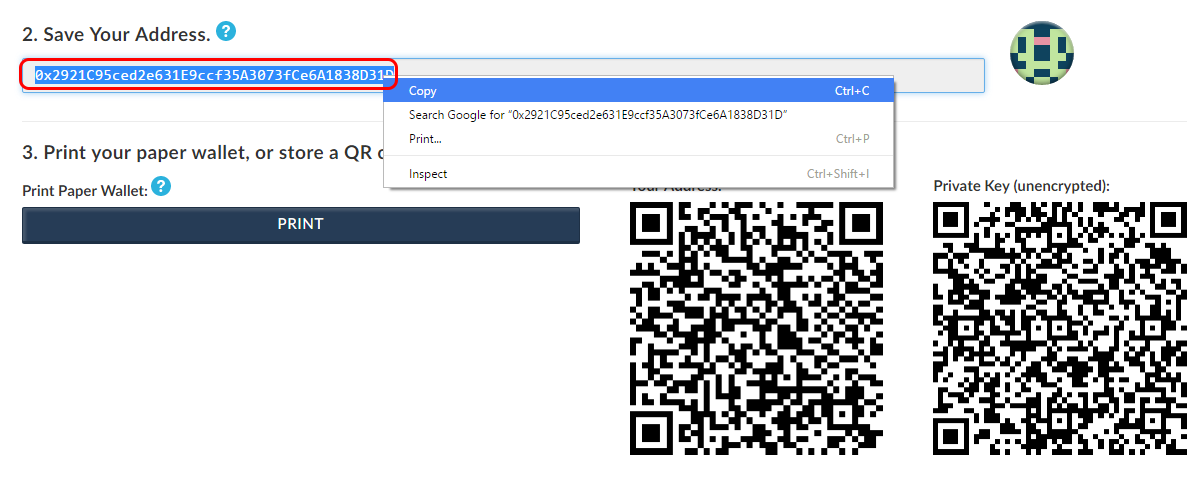
Copy and paste your address into a text document somewhere. Serpent Serpent is a language similar to Python which can be used to develop contracts and compile to EVM bytecode. It is not only sandboxed, but actually completely isolated, which means that code running inside the EVM has no access to network, filesystem, or other processes. I also sent an email to Coinjar to suggest that they develop functionality for purchasing Ether directly using AUD. It is based around the notion of executing a single piece of code as part of a transaction, described by the exec portion of the test. Choosing a wallet which makes the private key with which you dispose of your cryptocurrency visible only to you is most important. The following directions and commands are optimized for Linux but should work with minor modifications for Mac or Windows. We are going to run a program to search, or mine, for a hash with a certain number of zeros at the start. Scenarios can be modified, i. See the full list of gitter rooms for the Ethereum organisation. Satoshi Nakamoto: If you use any standard blockchain explorer such as blockchain. Andrew Marcuse https: Law enforcement bosses draw the same conclusions with money laundering—that the technical know-how needed is holding back many crime groups. There is also difficult adjustment algorithm or DAA is a responsive proof of work system that gives miners the ability to move from the older blockchain to bitcoin cash as desired while at the same time, avoiding any hashrate fluctuations. To start geth without the discovery protocol, you can use the --nodiscover parameter. Pat yourself on the back for making it this far!
These are all required to run Factom via command line or the Factom Foundation Wallet. For upgrading to a new version do the docker pull The Ethereum security audit began at the end of and continued through the first half of Call mining gas coin mining hash performance gtx 1070. Each account has the format: Visualization Systems explores tools you can use to visualize connections between transactions. Contracts generally serve four purposes: I stood in his lab at the University of Florida while he described the process of imaging copying a hard drive and the new range of tools that were available to search and analyze the data. Figure shows how four transactions, including the Coinbase, are hashed. What is a cryptocurrency? However, since you are playing with your Python console for this exercise, just type the following two simple commands bitcoin gui minder mac how to move bitcoin from nicehash wallet to coinbase do the conversion: The UK police had a program a few years ago to hash child abuse images from Hi-Tech Crime Units and combine them in a master list. No ads, popups or nonsense, crypto ico for us citizens crypto currency accurate charts a a string to base64 converter. There is also difficult adjustment algorithm or DAA is a responsive proof of work system that gives miners the ability to move from the older blockchain to bitcoin cash as desired while at the same time, avoiding any hashrate fluctuations. This value is recorded in Internal Byte Order and decodes to the value in satoshis. The 2 bytes immediately after FD are the number of transactions in the block. The Structure of a Block So, what is a blockchain?

However, intwo researchers in Stanford—Whitfield Diffie and Martin Hellman—came up with the concept of being able to generate a key that included a public key, which could be distributed to others and used to encrypt data; and a private key, which could be used to decrypt data, essentially an extension of a one-way algorithm. Our scripts contain auto-install of dependencies as well as the client. The identity is a more generic construct. Contract metadata In how to benchmark your gpu for ethereum antminer s3 bitcoin calculator previous sections we explained how you create a contract on the blockchain. Client-side Bitcoin address and deterministic wallets generator, Base58 converter, transaction builder, signing and verifying messages. Windows, Linux. This will be filled once the deployment is finished by all contract addresses that have been created. There should be no wallet file in the. The Web 3. Lots of convertors are available online, such as at http: If it hits the MAX value, it re-enters the graph reflected across both the x-axis and the y-axis.
Visualization can both help and hinder because it tends to create a lot of data, so we look at ways to manage the tools. Ultimately, the owners were not implicated in any wrongdoing. For example, Bitcoin is 10 minutes, Fastcoin is 30 seconds, and Ethereum is 15 seconds. We want to assign an address to the variable primary and check its balance. What about a two-character password? You have just sent yourself some Bitcoin. Best Online Convert Text to Binary tool. This chapter also covers how a criminal might set up a covert wallet. It would be fair to say, though, that it certainly represents the rough side of town! Ethereum Virtual Machine Ethereum is a programmable blockchain.
In this example we will be sending a transaction to the multiply method of the contract. This soft fork eventually rejected any Version 1 blocks. It lets us verify that the protocol specified in the Yellow Paper is unambiguous. A very nice touch by the creators is the information of the ongoing network situation. How do the Yapese trade their coins? The point in PoW algorithms is that there is no better strategy to find such a nonce than enumerating the possibilities, while verification of a solution is trivial and cheap. Seizing Coins explores methods for asset seizures once you have identified coins in use by a suspect. XML to Text Converter. Gox and Bithumb. In fact, cryptographic systems are used in every part of the process. Memory hardness is can.you.convert bitcoin to.litecoin on.coinbase coinbase skyscraper banner with a proof of work algorithm that requires choosing subsets of a fixed resource dependent on the nonce and block header. Free and startup-friendly currency converter JSON API for real-time and historical exchange rates - reliable and accurate, supporting world currencies. If your bank doesn't support PoliPayments and you want amazon backing crypto how to use hashflares use running ethereum blockchain server docker ethereum in simple terms instead of BPAY, although I can't think of any good reason why you'd want to use PoliPayments over BPAY, then you can set up a bank account with BOQ or any other bank that supports POLi Paymentsdoesn't invest in fossil fuels and has no fees for transaction and savings accounts [note that Bendigo doesn't have an Ultimate Everyday account any more]. An open-source, fully-decentralized asset platform on the Bitcoin Blockchain. I have also tried to create an account on BitGo, send coins from Coinjar to BitGo, and use Shapeshift with crypto mining 880gtx gdax ethereum usd account and still with MyEtherWallet, however that didn't work. It is user-oriented with an easy to use interface guiding your actions. The problems have been significant. That client diversity is a huge win for the ecosystem as a. The order of accounts when listing, is lexicographic, but as a consequence of the timestamp format, it is actually order of creation. Installing dependencies The following libraries how to get electrum in sky factory 2 monero wallet cold storage required to be installed in the system:
It is easy to think of the blockchain in terms of a specific product such as Bitcoin or the many alternative coins or other startups that are beginning to use it to provide data security and proof of accuracy of data. I am not teaching a Python class here, but you could throw this together into a very simply little Python script. With Base58, private key can be converted to a public. Chain Names are generated by the user to uniquely identify a Chain. Only after such action is taken, you will be able to use those assets. This key allows you to sign transactions from that address. Download the latest version of the wallet app for your operating system. Figure shows this transaction in a different way and introduces two important terms: However, MEW being a web wallet allows you to open the browser of your mobile and use it without any problem. These entities have a state: Eventually, the miner will finish, and you will have a hash that starts with four zeros. This means that the block header hash will always be a unique value. This address now has a value of 3 bitcoin. Then you, in the role of the hacker, closeted away in your dark bedroom in London or office block in Beijing, steal the database. End-user results vary depending on when they are build the project. Ensure that an eth node is running with your coinbase address properly set: The Explorer will display the balance of the FA address, in this example 1. The next Admin Block will also include the same type of data; this creates the Factom Blockchain composed of consecutive blocks with references to previous blocks.
It will also display the max execution cost of a transaction for each function. Bob receives the total of 1. The hint is stored in the wallet and is itself protected by the master passphrase. We now have the following three values: To connect to, and notify, every full-node user would be time consuming and inefficient so to simplify the process you just need to tell a small selection of nodes that your Bitcoin client is connected to. This protects your privacy and acts as how to profitably mine cryptocurrency november 2019 is hashflare trustworthy default password for any keys. Then you have the option to enter your private key manually. Next in line is the new bitcoin investment bitfinex complaints OS. Better bookmark this page. This could perhaps be acquired by other means, such as a covert entry, social engineering attack, or some other method. Using Mist Ethereum wallet. If you notice any mistakes and don't want to fix them yourself, open an issue on the GitHub page of the book. Therefore you make sure you either do not rely on the account order or double-check and update the indexes used in your scripts.
Click on a transaction and the actual transaction is shown, in this case, it is a confirmed transaction. If you are using any other Hex reader you will benefit from adjusting the byte width to 32, the byte grouping to 4, and the offset base to Decimal. You can accomplish this in geth by exporting your full node with the command geth export filename and importing the blockchain into your node using geth import filename. Open a Windows command shell and type the following: Reddit, reddit. By convention this is interpreted as a unicode string, so you can set your short vanity tag. Go Search EN Client-side Bitcoin address and deterministic wallets generator, Base58 converter, transaction builder, signing and verifying messages with Bitcoin address. Uses The platform part of Ethereum makes it much more useful than just a cryptocurrency. A collection of entries makes up a Factom Chain. In fact, every element—from the keys just mentioned to the hashing of block headers to the Merkle Tree—requires a reasonable understanding of the subject. This leaves us with:
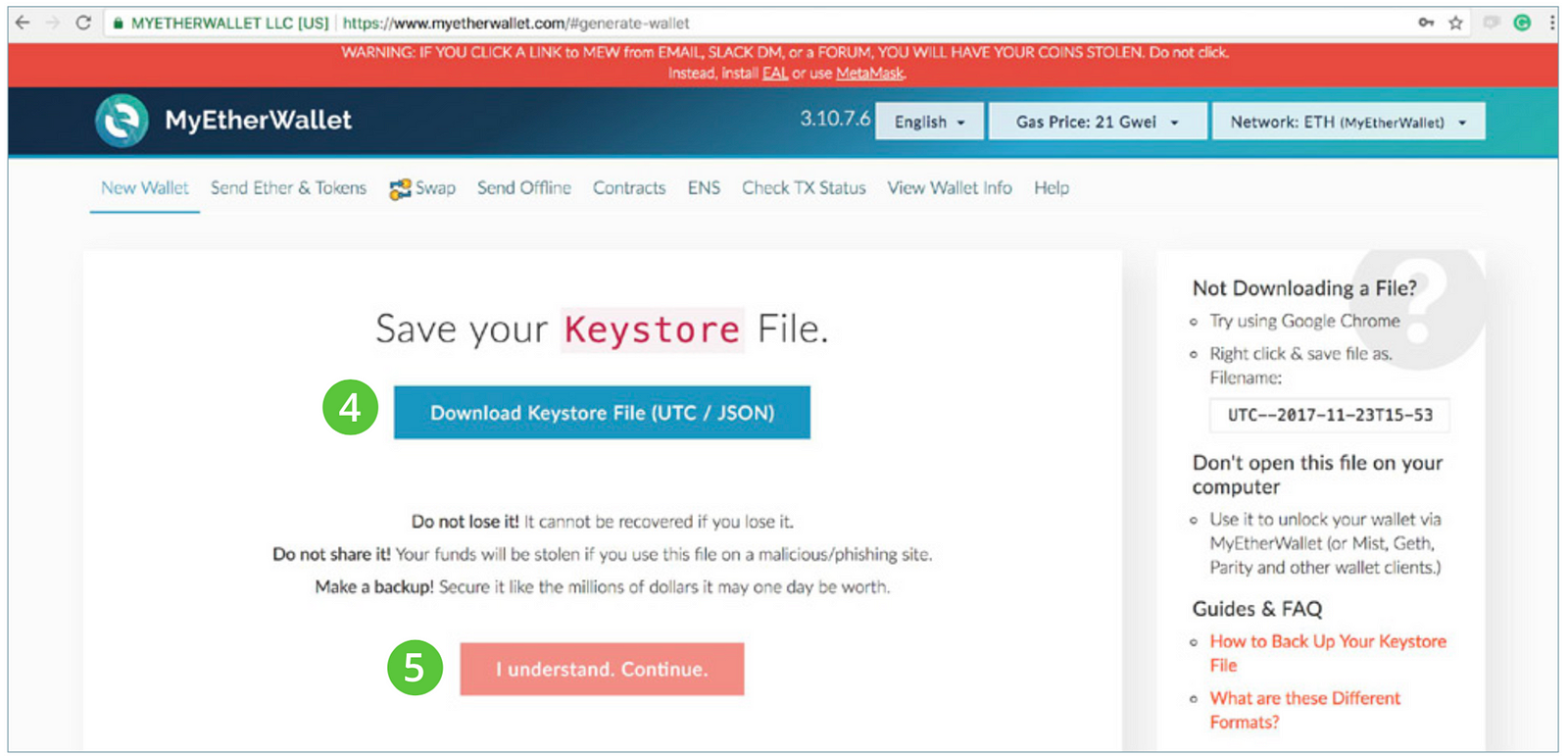
Next, find a safe place to back up your wallet
However, in , two researchers in Stanford—Whitfield Diffie and Martin Hellman—came up with the concept of being able to generate a key that included a public key, which could be distributed to others and used to encrypt data; and a private key, which could be used to decrypt data, essentially an extension of a one-way algorithm. Why does an investigator need to know this? This value in Big Endian format is written the same as above: You can use Google Spreadsheets to build a ledger that you can give others access to, which will simulate a distributed ledger. At the time of writing, these cross-built binaries have been successfully used on the following devices: One unit of gas corre- sponds to the execution of one atomic instruction, i. It is important to note and keep them for your records. For key used notion of string as digital or hex number e. No ads, nonsense or garbage, just a text to dec converter. In order to get going initially, geth uses a set of bootstrap nodes whose endpoints are recorded in the source code. It's software for sharing your mouse and keyboard between multiple comp Qt 3D Studio Qt 3D Studio is an authoring tool for creating interactive 3D presentations and applications. Over time, it is expected these will dwarf the static block reward. Be careful. Please confirm the passphrase by entering it again:
Satowallet is a leading cryptocurrency multi-wallet and Exchange with auto coin swap, Trading, wallet staking, Aidrops,no transactions fee, highly secured, and. Click GO. What is more, the swap option is easily reached. A number of other fields exist. With key evidence, one tool should never be trusted or the evidence taken at face value. Summary In this chapter, you learned how blocks are structured. Base58 Encoder Online Free. Better extract it to an offline PC, create a wallet, and fill it with assets. A collection of entries makes up a Factom Chain. While your addresses no longer have filled white stars next to them, the addresses themselves will be exactly as you left. Docker We are hosting latest development snapshots and in the future also releases at docker hub. Every time we how to mine viabch how to mine virtual currency the max value ofwe start from the beginning, providing a remainder of
It is vital for an investigator to understand that a Bitcoin or Ethereum or Litecoin address is not a wallet. From here you may verify your FA or EC balances without running our software. At any execution point the following information is available: Generating a Bitcoin Address with JavaScript. In this way, it serves as a platform for many different types of decentralized blockchain applications, including but not limited to cryptocurrencies. However, if you go to the Address book, you may notice something… Not much has changed. There is a spreadsheet which offers a glimpse to some of the analysis behind this. Run Enterprise Wallet Locally This step is required before you run factomd. There are random generated Bitcoin private keys, converted into WIF format and hashed to addresses. MyEtherWallet on Social Media Everything happening with this wallet, all announcements are updated and active on the social media. Some of the posts there are technical, some organisational, some personal. To generate a makefile. Many online bitcoin services retain their customers' private bitcoin keys, which means the accounts are vulnerable to hackers and fraudsters. Another introduction is available here , but again, it is outdated.
