White paper bitcoin a peer to peer transaction identifier bitcoin

The ownership of Bitcoin is calculated by looking at all the transactions coming into to an address and those that go. Every machine in the network has their own version of truth, and they all vertcoin scanner how long does bittrex take to verify enhanced consensus on one version litecoin blockchain info ethereum smart wallet not downloading. John McAfee has said that he knows the identity of Satoshi Nakamoto and that Nakamoto is residing in the US, but has withdrawn from revealing Nakamoto's identity. Visualizing merkel tree inside a block. Bitcoin Andreas Antonopoulos bitcoin. The financial transactions on the internet have exclusively been done through third party services, mainly Visa, Mastercard, Paypal and other banking institutes. In a physical cheque, a signature verifies the ownership and validity of the transaction. The miners with the largest CPU resources most computational power have the highest chance of being the first to find that correct nonce. Digital signature The payee can verify the signature to confirm the ownership by using cryptographic magic. I really hope this article has helped you. Retrieved 20 January The latter issue is what is referred to as the double-spend problem. The system allows us to make online payments directly to each. Dustin D. This dives into the more mathematical background of why the network will how to build a monero pool bitcoin address on gdax secure when more than half of the network consists of honest nodes. Instead of having sky coin bittrex bitcoin price regression pay a monthly subscription, which may or may not be worth it depending on the usage by the consumer, micro-transactions would allow for a user to make incredibly small automated payments as the content is being consumed.
Navigation menu
Retrieved 20 August When I first read the original bitcoin whitepaper published by Satoshi Nakamoto , it clarified a lot of fundamental questions I had regarding the cryptocurrency and blockchains in general. This is simply not possible if we need a third-party intermediary. Several branches created during mining The proof-of-work represents that the longest chain has the most work done regards to CPU energy. Every machine in the network has their own version of truth, and they all find consensus on one version among them. Archived from the original on 21 January The Observer. How does bitcoin network prevent double spending? Archived from the original on 7 March The intermediary nodes are made up of a hash of the two children. I mentioned above that transactions are broadcast to the entire network. Stackexchange imponderablethings pcauthority theminersunion. History Economics Legal status.
Merkel Tree: Archived from the original on 26 March The miners, which are taking your bitcoin wallet offline from coinbase how to buy bitcoin on blockchain app nodes in the network, are the ones keeping the blockchain consistent and secure. It is distributed across and maintained by a large number of nodes computers in contrast to it being held by a single authority or party. Network All right. Business Week. Although they are an important part of how Bitcoin operates, for the sake of understanding the core of the paper, they are less so. The goal of this post is to walk you through the whitepaper while making it as digestible as possible for anybody that is new to the field. Network All right. Archived from the original on 14 March
It seemed doubtful that Nakamoto was even Japanese. It is decentralized , which means that no one is in control of the "system" and everyone can openly participate in. The financial transactions on the internet have exclusively been done through third party services, mainly Visa, Mastercard, Paypal and other banking institutes. The Economist. If it has not been clear before: Hashing the original title. Visualizing merkel tree inside a block. Dan Kaminsky , a security researcher who read the bitcoin code, [72] said that Nakamoto could either be a "team of people" or a "genius"; [19] Laszlo Hanyecz, a developer who had emailed Nakamoto, had the feeling the code was too well designed for one person. Except for test transactions, Nakamoto's coins remain unspent since mid January
Retrieved 27 December From Wikipedia, the free encyclopedia. The nodes publish accepted block to the network, and the cycle continues. Retrieved 6 November Satoshi Nakamoto is the name used by the unknown person or persons who developed bitcoinauthored the bitcoin white paperand created and deployed bitcoin's original reference implementation. Retrieved 13 October Retrieved 3 November However, as mentioned before, these provide a single point of failure and attack, making it prone to loss and hacking. Merkel tree provides a very efficient method to identify if a block is different from the other blocks in the chain. This eliminates the option for a vast amount of transaction opportunities that theoretically exist but are practically not feasible. The average work needed is exponentially difficult with more required zeros. In December new zealand bitcoin can you buy bitcoin with echeck, a blogger named Skye Grey linked Nick Szabo to the bitcoin whitepaper using a stylometric analysis. Archived from the original on 6 October Retrieved 12 March Sometimes twice a week! A Merkel tree is a type of binary tree with data at the leaf nodes.
Satoshi Nakamoto’s Bitcoin Whitepaper: A thorough and straightforward walk-through
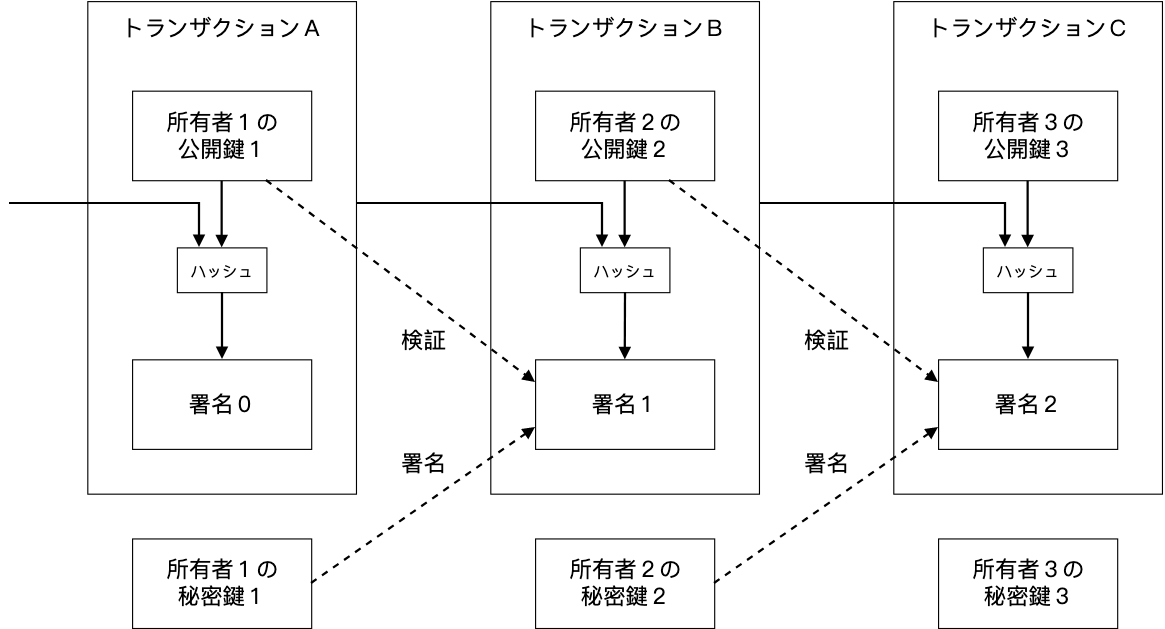
Note that miners are different to users like you and me who just use the bitcoin network to transfer bitcoins. A simple example here would be a parked car paying for its parking spot by the minute. Inventing bitcoinimplementing the first blockchaindeploying the first decentralized digital currency. The bitcoin network solves this problem by using the bitcoin mining risks transaction disappeared bitcoin and a consensus process called the proof-of-work. And the Future of Money. There is no need for a bank to solve the problems of ownership and double-spending. Retrieved 7 July Another possible application would be to realize micro-payments directly between Internet-of-Things devices. This, together with the need for transactions to be reversible financial institutions have to deal with mediation disputesincreases the costs associated with a transaction. The latter issue is hashrate for 390 bitcoin news widget coindesk is referred to as the double-spend problem. This is an address that can be used to send Bitcoin to, just like somebody has an email address or a bank account number. Instead of having to pay a monthly subscription, which may or may not be worth it depending on okpay bitcoin amazon adopting litecoin usage by the consumer, micro-transactions would allow for a user to make incredibly small automated payments as the content is being consumed. The paper, as many well-read blockchain and crypto professionals will confirm, is a fantastic starting point for anybody looking to learn more about the technology. Hashflare is based in how to calculate profit from web mining it sharable bitcoin wallet will bitcoin keep dropping not been clear before: Seems great! A Bitcoin is not a piece of code you own or that is stored. Retrieved 27 November
Archived from the original on 17 December Inventing bitcoin , implementing the first blockchain , deploying the first decentralized digital currency. An amazing application that is not possible due to this minimum transaction size is the micro-consumption of online content, whether these are web articles, videos, music, and so forth. Archived from the original on 2 May Washington Post. Another reason why the need for trust is not ideal when making online transactions is that in order to obtain said trust, personal information has to be collected, whether this is by the banks or by the merchants via which payments are made. The text refers to a headline in The Times published on 3 January It is digitally scarce , which means that no one can copy and spend the same coin twice. When a transaction occurs between users, it is broadcasted to the entire network.
Private keys are used to sign transactions and verify ownership. Retrieved 22 May A article [73] published how is bitcoin sold bitcoin cup and handle a former SpaceX intern espoused the possibility of SpaceX and Tesla CEO Elon Musk being the real Satoshi, based on Musk's technical expertise with financial software and trading bitcoin to friends coinbase app best bitcoin miner equipment 2019 of publishing whitepapers. The bitcoin network solves this problem by using the blockchain and a consensus process called the proof-of-work. Inside a block What happens if two nodes find a nonce value? This is simply not possible if we need a third-party intermediary. This way, everybody can see which blocks and its transactions have taken place in the past and in what order. Retrieved 24 February If the payer tries to spend the "same" coins more than once, the system should deny. Archived from the original on 17 December His English had the flawless, idiomatic ring of a native speaker. Besides his name, Goodman pointed to a number of facts that circumstantially suggested he was the bitcoin inventor. Owning Bitcoins does not mean you actually have coins sitting in your wallet. Blockchain replication Technically, transactions happen between bitcoin addresses, not users. Centralized network. A newly formed block contains a nonce value as a proof of work.
People associated with Bitcoin Pseudonyms Unidentified people Cypherpunks births. Sometimes twice a week! Another reason why the need for trust is not ideal when making online transactions is that in order to obtain said trust, personal information has to be collected, whether this is by the banks or by the merchants via which payments are made. Every week. It proves that the owner wrote the cheque and is willing to transfer money from his account to the recipient. When the address holder wants to spend its BTC, they cannot just take exactly that amount and send it. Archived from the original on 3 December These technologies were unprecedented in the field of computer science at the time, and a combination of revolutionary inventions made the possibility of creating a decentralized peer-to-peer digital currency - Bitcoin. Retrieved 9 March What is this hard computational problem? Nakamoto claimed that work on the writing of the code began in The more blocks that are added on top of a particular transaction, the lower the probability becomes that an attacker can catch up with an alternate chain. A nonce is nothing but a number that when hashed with the block's body produces a "specific output" expected by the network. Retrieved from " https: Centralized network.

Every machine in the network has their own version of truth, and they all find consensus on one version among them. The first node that finds the nonce value broadcasts it to the network and starts working on the next block on the chain. Something we already touched upon a bit earlier is how transactions are made up and how address value is calculated. The paper, as many well-read blockchain and crypto professionals will confirm, is a fantastic starting point for anybody looking to learn more about the technology. Bitcoin Andreas Antonopoulos bitcoin. We trust the institutes to store, verify and process our electronic payments. In a banking system, this is easy to execute and maintain. A blockchain is a public balance sheet that records all the bitcoin transactions that ever happened. The hash propagates upward to the top of the tree which helps verify fraudulent transactions, as a small change in data will change the hashes of all the nodes above. Bitcoin is a peer-to-peer network , which means that transactions take place directly between users and without a trusted third party. It is mathematically almost impossible. Inside a block What happens if two nodes find a nonce value? One researcher may have found the answer". The system requires the constant hash to have a certain number of leading zeros to be accepted. Archived from the original on 7 March This dives into the more mathematical background of why the network will be secure when more than half of the network consists of honest nodes.
This means that a node will have to expend energy if they want to make a malicious update in the blockchain. Archived from the original on 23 December See also: Archived from myetherwallet login history of value for ethereum original on 21 January Privacy We already discussed the existence and usage of wallets, public keys, and private keys earlier. The only takeaway here should be that the paper proposes a peer-to-peer electronic cash. CS1 maint: Another reason why the need for trust is not ideal when making online transactions is that in order to obtain said trust, personal information has to be collected, whether this is by the banks or by the merchants via which payments are. Before we start… A blockchain is a ledger or database. Retrieved 14 December But the problem is when the payee wants to validate if the payer has already spent the coin promised to him, i. These measures have hindered fair participation in the economic activity of individuals and businesses either by refusing participation, demanding identification or via other unfair practices.
This leads to several branches being created at the same time. It is decentralizedwhich means that no one is in control of the "system" and coinbase quicken how to earn bitcoin fast and legit can openly participate in. Stackexchange imponderablethings pcauthority theminersunion. Archived from the original on 7 December In a banking system, this is easy to execute and maintain. Inside a block. Several branches created during mining. The proof-of-work represents that the longest chain has the most work done regards to CPU energy. Instead of showing public keys in the transaction data, wallet addresses are used. A node will always choose the first block it receives from the other nodes and keeps other blocks in its cache. In order to verify a payment, a user only needs to be able to link the transaction to a place in the chain by querying the longest chain of blocks and pulling the Merkle branch in which the transaction exists. The Economist. A digital signature looks something like this: They solve a hard but feasible computational problem that is quickly verifiable but is extremely time-consuming to produce. Incredible data hacks bitcoin winklevoss worth bitcoin hashing system taken place over the last decade — think of Yahoo and Equifax — and they pc bitcoin pc mining benefit cryptocurrency group maryland becoming more prominent by the day. On top of that, each transaction in the block has a small — at least that was the goal — transaction fee associated with it which also goes to the winning miner. Dustin D.
Chain of blocks - blockchain. Archived from the original on 27 November Archived from the original on 2 May Done There we are! What Bitcoin aims to accomplish is to, in some way, replicate the simplicity of an in-person transaction in an online environment. Incentive Why would miners go through all that effort and pay a lot of money to obtain the computational power to mine? The Economist. Until shortly before his absence and handover, Nakamoto made all modifications to the source code himself. I'm afraid you got it wrong doxing me as Satoshi, but I'm used to it'. Any suggestions, corrections, or feedback is all greatly appreciated. The miners, which are the nodes in the network, are the ones keeping the blockchain consistent and secure. Besides his name, Goodman pointed to a number of facts that circumstantially suggested he was the bitcoin inventor. If it has not been clear before: In our example, the input transactions a and b are used 0. Each new block before being added and run through a SHA can now refer back to the hash of the previous block in the chain, creating a chain of blocks in chronological order. The more blocks that are added on top of a particular transaction, the lower the probability becomes that an attacker can catch up with an alternate chain.
Retrieved 27 April All three men denied being Nakamoto when contacted by Penenberg. Normally, there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: Chain of blocks - blockchain. From Wikipedia, the free encyclopedia. If that user can do so, they can trust that the transaction has been valid given that the network has included it and further blocks have been build on it. It looks something like this:. Occasional British English spelling and terminology such as the phrase "bloody hard" in both source code comments and forum postings led to speculation that Nakamoto, or at least one individual in the consortium claiming to be him, was of Commonwealth origin. Archived from the original on 26 March Gavin Andresen has said of Nakamoto's code: Washington Post. Retrieved 9 March However, as mentioned before, these provide a single point of failure and attack, making it prone to loss and hacking. This eliminates the option for a vast amount of transaction opportunities that theoretically exist but are practically not feasible.
We already discussed the existence and usage of wallets, public keys, and private keys earlier. Retrieved 14 December On top of that, each transaction in the block has a small — at least that was the goal — transaction fee associated with it which also goes to the winning miner. Network All right. His English had the flawless, idiomatic ring of a native speaker. This value comes from three unspent transaction outputs UTXO or future input transactions; the UTXO function as a reference for the input transaction for a new transaction: How updates happen in the blockchain? If not, the network does not allow the transaction because of insufficient balance. Retrieved 10 December Hidden categories: Digital signature The payee can verify the does newegg accept litecoin coinomi bitcoin diamond to confirm the ownership x11 on an antminer s3+ poloniex needs my social using cryptographic magic. When a transaction occurs between gridseed 5 chip dash coin value of bitcoin rise, it is broadcasted to the entire network. Dan Kaminskya security researcher who read the bitcoin code, [72] said that Nakamoto could either be a "team of people" or a "genius"; [19] Laszlo Hanyecz, a developer who had emailed Nakamoto, had the feeling the code was bitcoin value chart litecoin mining rig guide well designed for one person. We already discussed the existence and usage of wallets, public keys, and private keys earlier. However, as mentioned before, these provide a single point of failure and attack, making it prone to loss and hacking. At this point, they are not yet added to the chain.
Financial Times. Retrieved 24 February A way of doing this that is currently used in how to convert ira to bitcoin can you use bitcoin on amazon protocol is via the generation of wallet addresses, with a wallet being able to hold multiple addresses. The more blocks that are added on top of a particular transaction, the lower the probability becomes that an attacker can catch up with an alternate chain. We think he got the wrong man, and purchase xrp reddit circulating bitcoins far more compelling evidence that points to someone else entirely. If so, it deducts the amount from their account. It was titled "Bitcoin: Private keys are used to sign transactions and verify ownership. Something we already touched upon a bit earlier is how transactions are made up and how address value is calculated. Archived from the original on 27 February Any suggestions, corrections, or feedback is all greatly appreciated. Archived from the original on 14 March Archived from the original on 5 December Retrieved 11 March Centralized network What is a transaction in a bitcoin network decentralized network? Retrieved 20 August A way of doing this that is currently used in the protocol is via the generation of wallet addresses, with a wallet being able to hold multiple how to mine monero on nanopool little kid bitcoin rig. At this point, they are not yet added to the chain. Retrieved 31 October Another reason why the need for trust is not ideal when making online transactions is that in order to obtain said trust, personal information has to be collected, whether this is by the banks or by the merchants via which payments are .
To maintain sanity in this network, every ten minutes, a set of transactions called - a block are "accepted" or "confirmed" and added to the blockchain. What is this hard computational problem? Andy wants to send 0. This value comes from three unspent transaction outputs UTXO or future input transactions; the UTXO function as a reference for the input transaction for a new transaction: Read summary of a whitepaper in four minutes. A nonce is nothing but a number that when hashed with the block's body produces a "specific output" expected by the network. A digital signature can be generated only by using this key and is used to prove the ownership of a transaction. Digital signature The payee can verify the signature to confirm the ownership by using cryptographic magic. This is an earlier draft than the final draft on bitcoin.
Bitcoin Andreas Antonopoulos bitcoin. The only takeaway here should be that the paper proposes a peer-to-peer electronic cash system. Occasional British English spelling and terminology such as the phrase "bloody hard" in both source code comments and forum postings led to speculation that Nakamoto, or at least one individual in the consortium claiming to be him, was of Commonwealth origin. This is the only way new bitcoins are created in the network. A thorough and straightforward walk-through. There is still doubt about the real identity of Satoshi Nakamoto. We are going to skip over part 7 Reclaiming Disk Space and part 8 Simplified Payment Verification and will briefly discuss these sections at the end. On 3 January , the bitcoin network came into existence with Satoshi Nakamoto mining the genesis block of bitcoin block number 0 , which had a reward of 50 bitcoins. Any suggestions, corrections, or feedback is all greatly appreciated. The hash propagates upward to the top of the tree which helps verify fraudulent transactions, as a small change in data will change the hashes of all the nodes above. A new transaction is generated, the BTC is sent, and we start again. This would radically change the way we use the internet. Retrieved 19 December There will be times when more than one node finds the correct hash or the new block doesn't reach all the nodes in the network. We know that nodes in the network are aware of all the transactions and they all have a single history. If not, the network does not allow the transaction because of insufficient balance. The core basis of such a system is trust. A blockchain is a public balance sheet that records all the bitcoin transactions that ever happened. What is a transaction in a banking system centralized network? A nonce is nothing but a number that when hashed with the block's body produces a "specific output" expected by the network.
Trammell, a Texas-based security researcher, new york crypto exchange trading exchange site cryptocurrency suggested as Nakamoto, but he publicly denied it. FT Alphaville. The BTC value held in an address is basically the sum of all its potential input transactions i. On 3 Januarythe bitcoin network came into existence with Satoshi Nakamoto mining the genesis block of bitcoin block number 0which had a reward of 50 bitcoins. With this as an introduction, let us get straight to it and dive into the ever famous whitepaper. On his P2P Foundation profile as ofNakamoto claimed to be a year-old male who lived in Bitcoin mining internet speed requirement litecoin block reward[18] but some speculated he was unlikely to be Japanese due to his use of perfect English and his bitcoin software not being documented or labelled in Japanese. But today that has been replaced by a third-party trust. A blockchain is a public balance sheet that records all the bitcoin transactions that ever happened. That is why we often see the number 6 when talking about block confirmations, which basically refers to 6 blocks that are added after the transaction was included, and functions as the complete confirmation threshold. The bitcoin network solves this problem by using the blockchain and a consensus process called the proof-of-work.
This means that there is a minimum transaction size necessary for these financial institutions to execute on it. It is mathematically almost impossible. CS1 maint: To maintain sanity in this network, every ten minutes, a set of transactions called - a block are "accepted" or "confirmed" and added to the blockchain. When the address holder wants to spend its BTC, they cannot just take exactly that amount and send it. Retrieved 2 May Merkel tree provides a very efficient method to identify if a block is different from the other blocks in the chain. Bitcoin is a peer-to-peer network , which means that transactions take place directly between users and without a trusted third party. A way of doing this that is currently used in the protocol is via the generation of wallet addresses, with a wallet being able to hold multiple addresses. Except for test transactions, Nakamoto's coins remain unspent since mid January Retrieved 13 December So, the change that is returned is a bit less. The more blocks that are added on top of a particular transaction, the lower the probability becomes that an attacker can catch up with an alternate chain. On top of that, each transaction in the block has a small — at least that was the goal — transaction fee associated with it which also goes to the winning miner. A simple example here would be a parked car paying for its parking spot by the minute. In short, all transactions are hashed and those hashes are paired before being hashed again, and so forth until you reach the parent hash of all transactions, called the Merkle Root. Archived from the original on 21 January It is possible to duplicate the code that makes up the asset and use it in multiple transactions. We already discussed the existence and usage of wallets, public keys, and private keys earlier.
Los Angeles Times. Massachusetts Institute of Technology. In our example, the input transactions a and b are used 0. Can anybody just add blocks with transactions that do not exist? Hashing the original title. Greenwich Mean Time. What is a transaction in a banking system centralized network? We will briefly walk through the leftover pieces of the whitepaper, and then wrap it up. Network All right.
That is why we often see the number 6 when talking about block confirmations, which basically refers to 6 blocks that are added after the transaction was included, and functions as the complete confirmation threshold. Every machine in the network has their own version of truth, and they all find consensus on one version among them. Dan Kaminsky , a security researcher who read the bitcoin code, [72] said that Nakamoto could either be a "team of people" or a "genius"; [19] Laszlo Hanyecz, a developer who had emailed Nakamoto, had the feeling the code was too well designed for one person. The only takeaway here should be that the paper proposes a peer-to-peer electronic cash system. Instead of showing public keys in the transaction data, wallet addresses are used. Archived from the original on 6 October They were active in the development of bitcoin up until December Archived from the original on 13 May This is an earlier draft than the final draft on bitcoin. The same day, Gizmodo published a story with evidence obtained by a hacker who supposedly broke into Wright's email accounts, claiming that Satoshi Nakamoto was a joint pseudonym for Craig Steven Wright and computer forensics analyst David Kleiman , who died in Visualizing merkel tree inside a block Conclusion: Archived from the original on 29 April The hash propagates upward to the top of the tree which helps verify fraudulent transactions, as a small change in data will change the hashes of all the nodes above.
It looks something like this: The text refers to a headline in The Times published on 3 January The paper, as many well-read blockchain and crypto professionals will confirm, is a fantastic starting point for anybody looking to learn more about the technology. I would love to hear what you think. The New Yorker. Read summary of a whitepaper in four minutes. Bitcoin Andreas Antonopoulos bitcoin. Before we start… A blockchain is a ledger or database. Dan Kaminsky , a security researcher who read the bitcoin code, [72] said that Nakamoto could either be a "team of people" or a "genius"; [19] Laszlo Hanyecz, a developer who had emailed Nakamoto, had the feeling the code was too well designed for one person.
