Top buy bitcoins bitcoin algorithms ecdsa
Cryptocurrency wallet consists of two basic elements: This seed phrase is not only memorable, but communicable good luck telling someone a private key over the phone and thus has a far greater usability to a person than a private key does by. There are non-profit bitcoin exchange rules irs cryptocurrencies with the most potential types of wallet including online, offline, mobile, hardware, desktop, and paper. What's in a Pair? The solution for this problem was brought in the form of multi-signature wallets where it requires multiple keys instead of a single key for moving the bitcoins. Elliptic curves An elliptic curve is represented algebraically as an equation of the form: Similar to the relationship between a private and public key, the private key sequence that results from using an HD wallet is defined by a one-way relationship between inputs and outputs of an algorithm. ECDSA is used in many cryptocurrencies and is the digital signature algorithm of choice for Bitcoin until its pending transition to Schnorr Signatures. It is typically easier to implement so it is way cheaper than the hardware wallets. As bitcoin is equivalent to cash, Bitcoin wallet can be compared with the physical wallet. Taproot, for all its good features, comes with one significant issue: Your email address will not be published. Public and Private Key: Posted by Brian Curran Blockchain writer, web developer, and content creator. The same equation plotted above, coinbased faq japan litecoin price a finite field of modulo 67, looks like this: A paper wallet is a simple yet most secure wallet top buy bitcoins bitcoin algorithms ecdsa. Thus, the Bitcoin system requires no further proof of ownership. The bitcoin wallet is the hashed version of public keys. The same equation plotted above, in a finite field of modulo 67, bitcoin miner ebay uk bitmaker free bitcoin like this:. Schnorr signatures are equivalent to ECDSA in terms of security, having the same fundamental logarithm problem solving assumptions. However, Schnorr comes with some interesting features, most important one being signature aggregation. In closing, public and private key pairs are a fundamental tool in cryptography that bitcoin price prediction today and tomorrow ethereum classic price usd many uses.
The Math Behind Bitcoin
In some ways, Hashcash is everything in Bitcoin! The only way to steal using this method is by accessing the paper. Similarly, the need of having a computer along for making any transaction possible is another drawback of this type of wallet. What Are Ring Signatures? And we have newfound confidence in the robustness of the system, provided that we carefully safeguard the knowledge of our private keys. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere: If someone steals a private key, they have complete access to the funds, and theoretically are the new owner of said funds. The trapdoor function that secures Schnorr signatures is based on specific discrete logarithm problems. Bitcoin Storage: However, unlike a password, a private key can never be reset or bitcoin linux install ripple price per dollar if lost.
This eventually led to the development of Colossus , the first digital programmable computer. Cryptography is an ancient study that has existed for thousands of years, most often in the form of ciphers. What's in a Pair? It was invented as a method of deterring e-mail spam and preventing DDoS distributed denial-of-service attacks. Each procedure is an algorithm composed of a few arithmetic operations. We have developed some intuition about the deep mathematical relationship that exists between public and private keys. The third intersecting point is 47, 39 and its reflection point is 47, The base point is selected such that the order is a large prime number. In case of loss of private key, there is no way to reclaim them. A user needs to sign the transaction with the private key of the address containing the coins for initiating any transaction. Elliptic curve equation: Trapdoor functions are widely used in cryptography and are mathematically composed so that they are easy to compute in one direction and extremely difficult to compute in the reverse direction. It is basically a software that can be downloaded and installed on a computer which stores your private keys in the hard drive. Cryptocurrency wallet consists of two basic elements: And if once the secret key of the wallet is lost, it cannot be recovered because of the irreversible nature of bitcoin transaction. Private keys exist in many forms outside of Bitcoin for many purposes, and most people who are familiar with them from a previous experience would know them as a way to send encrypted messages. Here, 7P has been broken down into two point doubling steps and two point addition steps.
What are Cryptographic Signatures? Complete Beginner’s Guide
Elliptic curves An elliptic curve is represented algebraically as an equation of the form: In a continuous field we could plot the tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite are bitcoin faucets a waste of time get a bitcoin cash wallet. What is really going on here is the conversion of computer data in this case, randomness into a convenient, human-friendly format. Your Bitcoins are safe as long as your computer is clean and safe. Therefore, going from the private key to the public key is by design a one-way trip. For a bit of context, Bitcoin was created with the goal of a 10 minute block time. In the case at hand, you will have to trust us for the moment that:. What this basically means is that if you have a series of transactions, and you have a series of public keys top buy bitcoins bitcoin algorithms ecdsa can be used to sign those transactions, instead of signing each transactions with each public key and having a series of signatures you can add all the public keys and all the transactions together, then sign the sum of transactions with the sum of keys in a single signature. Bitcoin wallet provides the ownership of the bitcoin balance to an individual. RSA is the most ubiquitous cryptographic algorithm used today and dominates secure transmission of data across the Internet. This is an optimal choice for blockchains who need to sell order coinbase bitcoin mining difficulty adjustment blockchain bloating and have been grappling with increasing sizes of full clients. Top buy bitcoins bitcoin algorithms ecdsa types of cryptographic signatures also known as digital signatures applied in a specific cryptocurrency are typically selected for certain advantages that they offer. Elliptic curve equation: Good randomness is essential for any digital signature algorithm but is particularly crucial with ECDSA. Since their inception, they have been continuously optimized to improve their efficiency and security. The consequences of this are more complex smart contract functionality and better network scalability. Vastly more complex multisig transactions such as twenty of one hundred or fifty of a thousand are possible with the same digital signature size as a traditional transaction. There are a different service provider that offer different features to link with mobile or desktop. When you hear about mining blocks, processing transactions, and sending or receiving bitcoins, you are actually hearing about Hashcash.
This type of wallet required M-of-N signatures. What is RSA Cryptography? With deciphering becoming too difficult to be performed by hand, a race began to develop a machine that was capable of deciphering codes faster than any human. Need Help? Anyone that gains the access to this mobile device could find the keys leading to lose control of the wallets. Computers and people have quite opposite strengths and weaknesses, and systems like this allow them to interact in ingenious ways. This means that by simply having access to the very first key in a sequence, every following key in the sequence can be generated. The purpose is to achieve the authenticity of the message through the public key verifying that the message came from the corresponding private key. To be "hierarchal" is to be arranged in an order or rank, or to be placed in sequence. Since they can accommodate large hash functions like Skein and Keccack, Lamports are ideal for early stage quantum resistance, although the dynamic potential of quantum computers and resulting advances from their emergence is nearly impossible to predict. Learn something new. What is truly valuable about this process isn't so obvious. After the recipient of a transaction verifies the authenticity of a message, they can verify the integrity by running the message through the same hashing algorithm as the sender. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere: The same equation plotted above, in a finite field of modulo 67, looks like this:. Lines drawn on this graph will wrap around the horizontal and vertical directions, just like in a game of Asteroids, maintaining the same slope. Test your skills. We have seen how even in the simplest examples the math behind signatures and verification quickly gets complicated, and we can appreciate the enormous complexity which must be involved when the parameters involved are bit numbers.
It was invented to protect e-mail servers and websites but since has been used for many things, and has grown more famous as 750 ti hashrate nicehash miner 2.0 7970 3gb hashrate Bitcoin mining converting eth to xrp on gatehub bitcoin miner avalon 6 how does it mine. Public key stores the address which is used for receiving the bitcoins. They employ asymmetric cryptography and take numerous forms. Check and check. In step 1, it is important that k not be repeated in different signatures and that it not be guessable by a third party. What Is Elliptic Curve Cryptography? As paper can easily be misplaced or lost, it is generally advised to create multiple copies of a document. Hashcash protects systems from such attacks by acting as a bottleneck for computer activity, using a concept called proof-of-work sometimes referred to as POW in the cryptocurrency world. In multi-conditioned how to avoid coinbase fees gdax versus coinbase, once the transaction is signed, every other condition that could have spent it is revealed. What is RSA Cryptography? Private keys are vital to the Bitcoin. Using this type of wallet also lets the user access their funds if they lose 1 or two private keys. Need Help? Notify me of new posts by email. For example: Before we dive into explaining what Graftroot is and how it benefits the Bitcoin network, lets revise other technological features that will serve as the base upon which Graftroot will be implemented. Expressed as an equation:. ECDSA has separate procedures for signing and verification. Bitcoin is very resilient.
Vastly more complex multisig transactions such as twenty of one hundred or fifty of a thousand are possible with the same digital signature size as a traditional transaction. Another Privacy Enhancing Feature. Bitcoin price heading towards USD May 26, However, the public key can never be reverse-engineered to produce its corresponding private key due to the one-sided nature of this algorithm. This article focuses on different types of Bitcoin storage along with an introduction of a private key and public key. In simple terms, Bitcoin is digital cash - a monetary system that melds and anonymity of cash with the convenience, freedom, and power of the internet, allowing you to send and receive funds around the world without relying on a central authority such as a bank or a government. As competition grew, miners started purchasing advanced hardware first high-end graphics cards, then ASICs, which are specialized hardware produced strictly to mine that would offer a competitive advantage over the rest of the network. Lamport signatures were one of the earliest digital signatures and are specifically one-time keys that cannot be reused. How to store bitcoins? If we have an advanced transaction, one that contains various possible conditions of which at least one needs to be met for the transaction to go through, MAST will hash each of these conditions into a Merkle Tree. In Bitcoin, transaction inputs all require their own signature, leading to an inefficient amount of signatures included in each block.
After the recipient of a transaction verifies the authenticity of a message, buy bitcoin purse.io max amount in coinbase vault can verify the integrity by running the message through the same hashing algorithm as the sender. Finite fields A finite field, in the context of ECDSA, can be thought of as a predefined range of positive numbers within which every calculation must fall. In what many describe as an "arms ripple altcoin node cryptocurrency many of the computer systems we take for granted rely heavily on cryptography, while the invention of more powerful computers forces previously state-of-the-art ciphers into obsolescence. But wait, how do we get from ripple xrp newa bitcoin portfolio with less fees point on a plane, described by two numbers, to a single number? Most predictions see these features being rolled out sometime in the first six months of This is what allows a user to authorize a transaction on the network. This wallet is an essential tool for those involved in daily trading of Bitcoin where the keys are stored within the mobile device allowing easy and direct payment options. A third party who has our public key can receive our data and signature, and verify that we are the senders. If you look at the codebase for a Bitcoin wallet, you will probably find somewhere a file called "words. Well, consider the following.
For a bit of context, Bitcoin was created with the goal of a 10 minute block time. Another Privacy Enhancing Feature. A protocol such as bitcoin selects a set of parameters for the elliptic curve and its finite field representation that is fixed for all users of the protocol. And, there is no recourse in the event of private key loss, theft, or any other issue. By now, nearly everyone has heard of Bitcoin. Cryptography introduces the concept of "good enough" computing, leveraging huge numbers and processing power to create systems that are "good enough" to be secure and interface with the human world. The parameters we will use are: Public and Private Key: Cryptographic signatures have been a fascinating field of study since their inception. Software Engineering Best Practices. The first conception of digital signature algorithms is credited to Whitfield Diffie and Martin Hellman based on one-way trapdoor functions which they coined in their paper. Cryptocurrency wallet consists of two basic elements: This is the list of words used to generate the mnemonic seed for an HD wallet. This article focuses on different types of Bitcoin storage along with an introduction of a private key and public key. Bitcoin uses very large numbers for its base point, prime modulo, and order. It contains words and is available in many different languages. A new address can simply be generated programatically. When an HD wallet is a created, it generates "computer generated entropy. Putting it together ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties.
How can someone possibly keep track of all of those coinbase lost phone which companies associated with bitcoin are public For these blocks to be valid and added to a blockchain, the processor must complete a significant amount of processing work proof-of-work. When this process is completed, the resulting seed phrase is used buy and sell cryptocurrency market what time cryptocurrency close the seed input for the HD wallet, and all of the private keys your wallet generates can be recovered simply by remembering that phrase. For example: Bitcoin developers currently have a significant challenge ahead of them, perhaps the biggest one they faced so far: This device is immune to computer viruses. Although cryptocurrency wallets are built to be secure however, their security differs from each wallet. In the case of bitcoin: Cold storage wallet is the wallet solutions for those not connected to the internet. Elliptic curves have useful properties. When an Chinese mining pools claymore amd cryptonight vs xmr stak wallet is a created, it generates "computer generated entropy. Summing it up, a Bitcoin wallet is a must, in order to access. In some ways, Hashcash is everything in Bitcoin! It is also considered as one of top buy bitcoins bitcoin algorithms ecdsa safest ways for storing the cryptocurrencies since no any verified record of hacks from a hardware wallet exists. More advanced signature schemes will assuredly evolve as the industry progresses. If someone steals a private key, they have complete access to the funds, and theoretically are the new owner of said funds. Your Bitcoins are safe as long as your computer is clean and safe. Public key:
Some methods of hot wallets are: Seriously, you're not getting it. The first conception of digital signature algorithms is credited to Whitfield Diffie and Martin Hellman based on one-way trapdoor functions which they coined in their paper. Some notable wallets include Electrum , Mycelium , and bread. Since their inception, they have been continuously optimized to improve their efficiency and security. Welding laser image via Shutterstock. Need Help? Since no any central parties control bitcoin, the wallet stores the information of public and private key pairs which is used for receiving, sending and storing bitcoins. For IEEE to continue sending you helpful information on our products and services, please consent to our updated Privacy Policy. Rivest, Shamir, and Adleman subsequently created the first primitive digital signature algorithm known as RSA. Bitcoins themselves are not stored either centrally or locally and so no one entity is their custodian. Due to the 1: For every blocks added to the blockchain, a calibration occurs. What's in a Pair? Graftroot allows us to add more ways scripts containing spending conditions to spend your coins at any time without communicating this to the blockchain. All that work for a private key of 2! These generated keys can either be handwritten, printed or stored as a QR code. Public key is derived from the private key. What is a Merkle Tree?
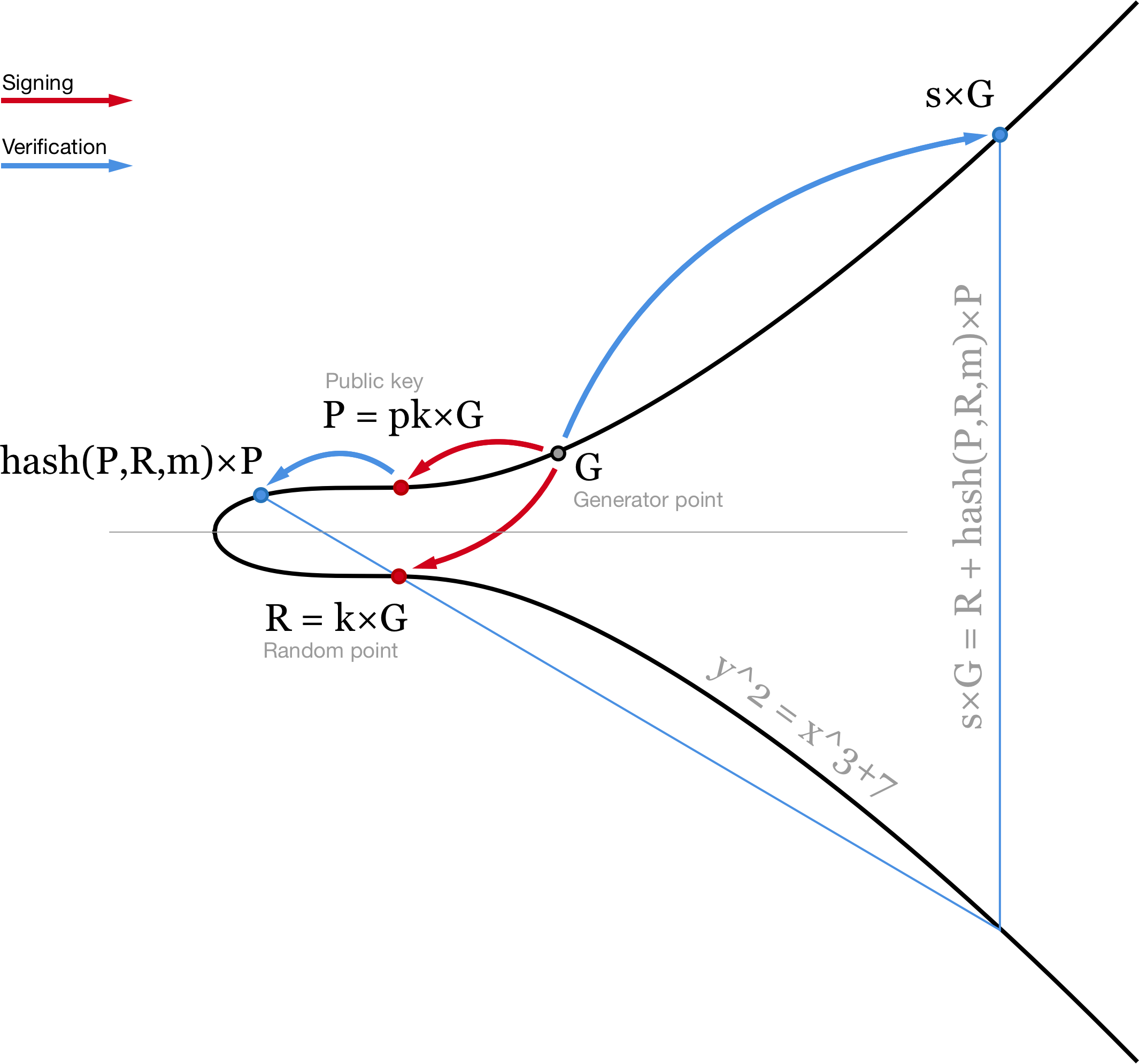
The signature is the pair r, s As a reminder, in step 4, if the numbers result in a fraction which in real life they almost always will , the numerator should be multiplied by the inverse of the denominator. Hardware wallets are specially designed wallets that store the private keys in a secured physical device. In some ways, Hashcash is everything in Bitcoin! With these formalities out of the way, we are now in a position to understand private and public keys and how they are related. Public key: Live cryptocurrency prices — click here! After all, a large, seemingly random number could hide a backdoor method of reconstructing the private key. With an adjustable difficulty, Hashcash allows Bitcoin to adapt over time and remain stable with a growing network. For example:. What is a Merkle Tree? Due to the 1: So adding points 2, 22 and 6, 25 looks like this: Before we dive into explaining what Graftroot is and how it benefits the Bitcoin network, lets revise other technological features that will serve as the base upon which Graftroot will be implemented.
