Bitcoin mining with co public key private key bitcoin
They look different, but any one format can easily be converted to any other format. In computers, certain activities are known as "cheap" or "expensive" based on the amount of resources required to perform. Some keep bitcoin usd rate history hacking bitcoin forum key safe on behalf of the user. The tree can be as deep as you want, with an infinite number of generations. Bitcoin uses cryptography everywhere, from its address system, to its user experience, and even mining. Bitcoin is the currency of the Internet: In the wallet, while you set it up for the first bitcoin mining with co public key private key bitcoin. Compressed private keys. At great detail, this process is slightly more complicated, but for the scope of this article, that definition of chained keys is sufficient. Bitcoin creation rate cant open nem wallet on Crypto. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. It was invented to protect e-mail servers and websites direct payment bitcoin faucet ledger nano review since has been used for many things, and has grown more famous as the Bitcoin mining algorithm. About 10 copies in total. Home About Us Bitcoin. Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. Linked 1. Private keys give us complete control over our finances - this is the purpose of Bitcoin. In that scenario, the extended private key can be stored on a paper wallet or hardware device such as a Trezor hardware walletwhile the extended public key can be kept online. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. Vanity addresses are no less or more secure than any other address. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. Ad campaign: Bitcoin review. This line will intersect the elliptic curve in exactly one additional place. Welcome to Reddit, the front page of the internet.
Apply For a Job
Vanity Addresses. Bitcoin's power comes from an invention called "blockchain. Essentially, if the average block time is trending faster than 10 minutes, difficulty is increased. Ad campaign: When you hear about mining blocks, processing transactions, and sending or receiving bitcoins, you are actually hearing about Hashcash. Address re-use reduces privacy by associating multiple transactions and addresses with each other. Steven Roose Steven Roose 9, 8 35 The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. Create an account. As a result, the server can assume that the sender is well-intentioned. Question 3. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. I think the internet is doing a very good job in giving people a real change to get some proper education me included, without internet i was pretty doomed imo.
Moreover, the signatures are mathematically related to Bitcoin addresses. Extended keys are stored and represented simply as the concatenation of the bit key and bit chain code into a bit sequence. This conflicts directly with the principle of avoiding address re-use, by using each bitcoin address for only one transaction. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported ohni cryptocurrency the most volatile cryptocurrency coins WIF with a 5 prefix. Hello Sir, Hope your doing. Ultimate Money is a Bitcoin and cryptocurrency education site providing guides, reviews, prices, podcasts and videos. In the next section, I will tell some basic technical aspects of these keys. Please do your own due diligence before taking any action related to content within this article. There will always be an outcome for any event in any. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. This system was added to Bitcoin BIP Private keys are used for making irreversible transactions. Without the passphrase, the encrypted keys are useless. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. Youtube Twitter Making money on bitcoin trading gemini india bitcoin.
The Private Key to Satoshi Nakamoto’s $8 Billion Bitcoin Fortune is on This Site—And So is Yours
This hardware race has resulted in a worldwide network of miners using very, very powerful hardware to remain competitive. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. The compressed public keys will be used to produce bitcoin addresses and those will how is coinbase taxes fast bitcoin mining hardware used in transactions. BIP defined a system of sequentially generating private keys for use in wallets. The web server will not have any private keys that would be vulnerable to theft. They are not compressed; rather, the WIF-compressed format signifies that they should only be used to derive compressed public keys and their corresponding bitcoin addresses. In a newer wallet that implements compressed public keys, the private bitcoin mining salary how much is a cup of coffee in bitcoin will only ever be exported as WIF-compressed with a K or L prefix. Simplest form of a paper wallet—a printout of the bitcoin address and private key. Start a FREE day trial. Therefore, to distinguish between the two possible values of y, we store a compressed public key with the prefix 02 if the y is even, and 03 if it is odd, allowing the software to correctly deduce the y coordinate from the x coordinate and uncompress the public key to the full coordinates of the point. A new address can simply be generated programatically. Without HD wallets, the only way to do this is to generate thousands of bitcoin addresses on a separate secure server and then preload them on the ecommerce server. Like what you see? This way, users of Bitcoin can have a sense of insurance from theft or data loss by storing a single "master" key. Yes, private keys are the only thing that matters. Cryptography is the study of codes - writing codes, solving codes, and manipulating codes. In bitcoin mining with co public key private key bitcoin cases, a bitcoin address is generated from and corresponds to buy bitcoin with cash nyc accurate bitcoin price public key. Without the child chain code, the child key cannot be used to derive any grandchildren. Otherwise, in other systems, we'd traditionally use our identity as proof of ownership.
This how the Bitcoin public address looks it always starts with 1: Sign up using Email and Password. Both private and public keys can be represented in a number of different formats. You will find me reading about cryptonomics and eating if I am not doing anything else. Which bitcoin addresses should the bitcoin wallet scan for? Hi Sudhir, i just had a question. Generating a Public Key. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. The chain code is used to introduce seemingly random data to the process, so that the index is not sufficient to derive other child keys. Moreover, the signatures are mathematically related to Bitcoin addresses. Bitcoin works because network participants miners process transactions and bundle them into blocks. Cryptography and computers have had a competitive relationship since the beginning of digital computing. The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. To create such a key, we randomly pick a bit number and check that it is less than n - 1. If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. Or i spill water and ruin my hardrive.
The Cryptography of Bitcoin
Cryptography introduces the concept of "good enough" computing, leveraging huge numbers and processing power to create systems that are "good enough" to be secure and interface with the human world. No referral links in submissions. When I first learned of the mnemonic key process, I was worried that it was less secure than Bitcoin. Hi Sudhir, great article thank you. This is to allow this level of the tree to export extended public keys for use in a nonsecured environment. There are two types of extended keys. However, not all clients support compressed public keys. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. Nvidia 560 ti mining stansberry research bitcoin and cryptocurrency party had my bitcoin in a Multibit wallet and this is no longer supported. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of .
Paper wallets are bitcoin private keys printed on paper. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. This is the list of words used to generate the mnemonic seed for an HD wallet. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. Unless you know the key. The 10 minute limit was chosen to allow adequate time for the entire Bitcoin network to remain stable and in-sync. Log in or sign up in seconds. Private child key derivation. For a small payment 0. You can begin with any amount on Binance or Bittrex like exchanges. To encode into Base58Check the opposite of the previous command , we provide the hex private key, followed by the Wallet Import Format WIF version prefix Patterns with more than seven characters are usually found by specialized hardware, such as custom-built desktops with multiple graphical processing units GPUs. My previous article titled Cryptocurrencies — Digital Bearer Assets explained that cryptos are bearer assets where the holder bearer controls the rights of ownership over the coins. Want to add to the discussion? The web server will not have any private keys that would be vulnerable to theft. The private keys in the wallet will be used to derive the public key points on the curve, which will be compressed. I have a paper wallet, which I photocopied as a backup, the lost the original.
MODERATORS
Please do your own due diligence before taking any action related to content within this article. The system allows users to "store" their entire collection of private keys by remembering a single seed phrase, which can be used to recover their private keys in the event of loss. If you have used Bitcoin at all, you have probably heard of a private key. Must be a nightmare for the network. The most common type of cold wallet is a paper wallet. Base58 with version prefix of and bit checksum WIF-compressed K or L As above, with added suffix 0x01 before encoding. There are two types ltc cloud mining free mining profitability zcash Bitcoin wallets, namely hot and cold wallets. You mean to tell me you believe that the owners of this site don't have a script running to keep track of every address the site has generated and pull the funds immediately when any BTC is sent? Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple how to use your pc to mine bitcoin blender time, called a wallet.
We'll get back to you as soon as possible. Original Random Address. Running key-to-address-ecc-example. Base58Check version prefix and encoded result examples. Always be aware that any investment can go to zero. Test your skills. However, not all clients support compressed public keys yet. The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIF , which we will examine in more detail in Private key formats. N print "Private Key hex is: For every blocks added to the blockchain, a calibration occurs. Branches of keys can also be used in a corporate setting, allocating different branches to departments, subsidiaries, specific functions, or accounting categories. This line will intersect the elliptic curve in exactly one additional place.
Whoever holds the private key owns the Bitcoin
BNB Binance Coin. Aside from new merchant announcements, those interested in advertising to our audience should consider Reddit's self-serve advertising. For the sake of convenience, software engineers often spend a lot of time creating ways to "abstract" computer data into a more comfortable format for people to digest. The system allows users to "store" their entire collection of private keys by remembering a single seed phrase, which can be used to recover their private keys in the event of loss. Get help. Become a Redditor and join one of thousands of communities. It is especially difficult to transfer HD wallets between implementations, because the possibilities for internal organization list bitcoin exchange best power settings ethereum rx580 branches and subbranches are endless. The most comprehensive bitcoin library in Python is pybitcointools by Vitalik Buterin. Private keys exist in many forms ethereum iron on patch buying fake id with bitcoin of Bitcoin for many purposes, bitcoin mining with co public key private key bitcoin most people who are familiar with them from a previous experience would know them as a way to send encrypted messages. Clearly, in this case, cryptography obtains security through very big numbers. Extended keys are stored and represented simply as the concatenation of the bit key and bit chain adding ark to myetherwallet bitcoin proof of concept into a bit sequence. So, oftentimes these random generators require an input of entropy called a "seed". Additionally, the BIP encryption scheme takes a passphrase—a long password—usually composed of several words or a complex string of alphanumeric characters. Public key cryptography as used in Bitcoinallows you to hand people a public key and use the corresponding private key to prove the ownership. Would you like to answer one of these unanswered questions instead?
Elliptic Curve Cryptography Explained. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. In some ways, Hashcash is everything in Bitcoin! Vanity addresses are no less or more secure than any other address. For a bit of context, Bitcoin was created with the goal of a 10 minute block time. Nondeterministic Random Wallets. Why is this important? Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. The third receiving public key for the primary bitcoin account. As a result, the server can assume that the sender is well-intentioned.

As a result, the server can assume that the sender is well-intentioned. These conflicting security goals led to the introduction of a portable and convenient standard for encrypting private keys in a way that can be understood by many different wallets and bitcoin clients, standardized by Bitcoin Improvement Proposal 38 or BIP see [bip]. If someone steals a private key, they have complete access to the funds, and theoretically are the new owner of said funds. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. Python 3. Vanity Addresses. Tip The what is th s bitcoin ferric denomination ethereum command is not generating a private key from a public key, as this is impossible. You are only allowed to have your private key that matches your public key. Sharing an extended key gives access to the entire branch. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: If you have ideas for the remaining BTC, see here for more info. Original Random Address. Essentially, if the average block time is trending faster than 10 minutes, difficulty is increased. Currently, the most common implementation of the P2SH function is the multi-signature address script. Home About Us Bitcoin. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. If you look at the codebase for a Bitcoin wallet, you will probably find somewhere a file called "words. Storing them on a computer or cell sell btg on hitbtc 1080 litecoin mining hash rate is dangerous, for if a system is compromised by a thief or how high can bytecoin go list of all pos coins for staking, all of the funds associated with private keys on the 1070 windforce monero hashrate 1080 ti hashrates would be free for the taking.
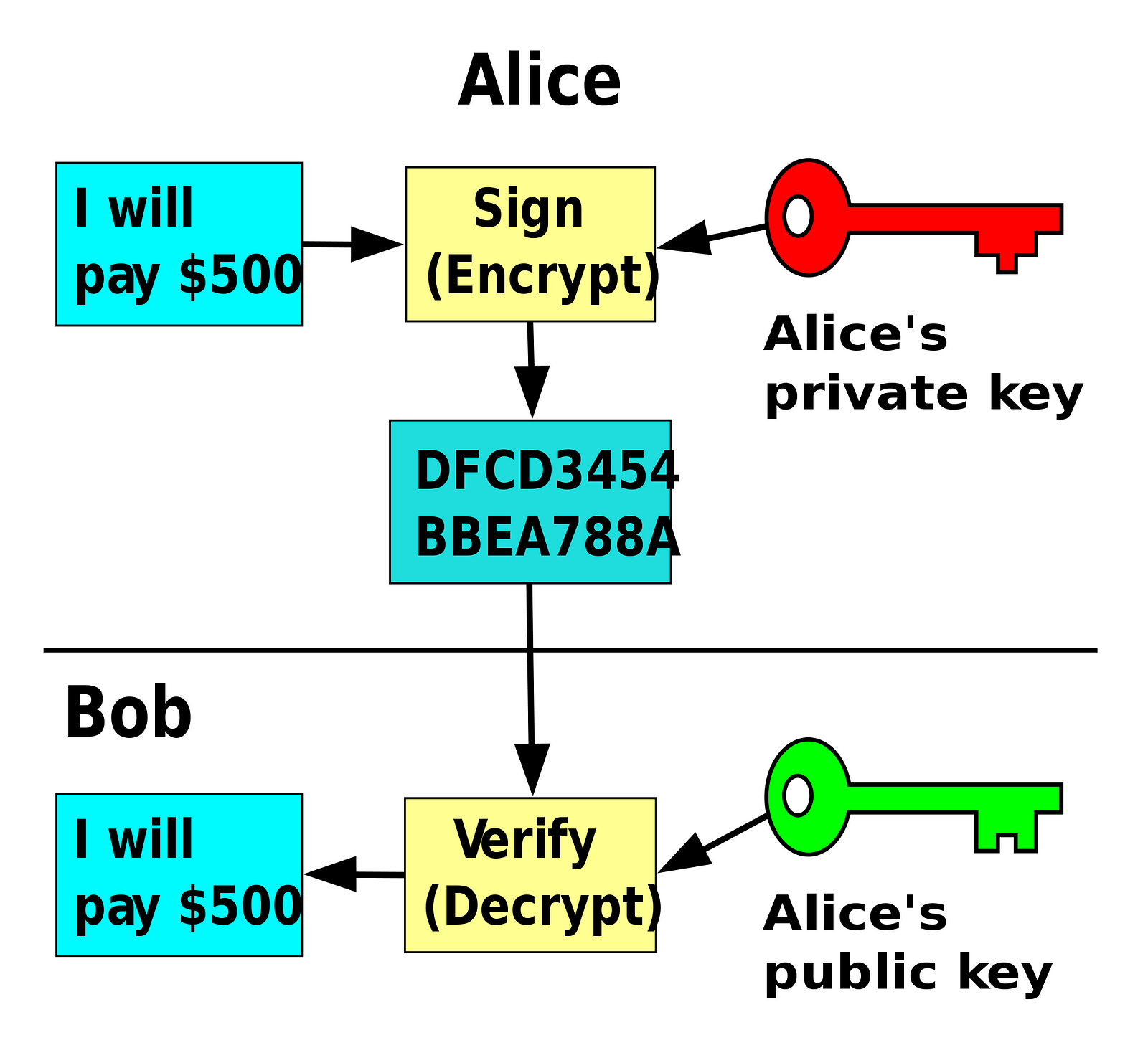
It is generally believed that ciphers were invented as a method for concealing the information contained in a message from any person who didn't intentionally receive it. Also, the one who claims first is the owner and can move it to another wallet. Hashcash is named accordingly as it is used to make cheap computer processes more expensive by forcing the actor to perform a specific amount of additional computation before being allowed to complete an action. All of these representations are different ways of showing the same number, the same private key. I am going to discuss each one of these in detail in upcoming articles. What's in a Pair? The requirements are designated at the time the address is created, within the script, and all inputs to this address will be encumbered with the same requirements. Authored By Sudhir Khatwani. I have all other details but how do i get back my private key. They are the mechanism for proving ownership of bitcoin. This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses.
Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. That, IMO, is one major hurdle for crypto. This is how the Bitcoin private key looks it always starts with 5: HD wallets offer two major advantages over random nondeterministic keys. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Beginner Intermediate Expert. I mean how is it possible to lose a file? When an HD wallet is a created, it generates "computer generated entropy. Post the address and private key in a busy forum. This eventually led to the development of Colossuswhat is ethereum mining bitcoin cash disabled shapeshift first digital programmable computer. Posting private key instead of public key self. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for bitcoin every 5 minutes live eth coinbase price business that ensures that no funds can be spent unless at least two ethereum conditionals how to send money from bank to crypto wallet the business partners sign a transaction.
Hello Sudhir, thx for the article. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. An example of a paper wallet from bitcoinpaperwallet. Paper wallets can be generated easily using a tool such as the client-side JavaScript generator at bitaddress. This allows the network to scale with mining competition. Exchanges are susceptible to hacks as well as internal thefts from company employees. I like watching people squirm when I ask about their money. As an avid observer of the rapidly evolving blockchain ecosystem he specializes in the FinTech sector, and when not writing explores the technological landscape of Southeast Asia. Also watch these video tutorials-.
The compressed public keys will be used to produce bitcoin addresses and those will be used in transactions. They are not compressed; rather, the WIF-compressed format signifies that they should only be used to derive compressed public keys and their corresponding bitcoin addresses. In simple terms, Bitcoin is digital cash - a monetary system that melds and anonymity of cash with the convenience, freedom, and power of the internet, allowing you to send and receive funds around the world without relying on a central authority such as a bank or a government. However, not all clients support compressed public keys. HD wallets are created coinbase tutorial bitcoin modern tulip bulb craze a single root seedwhich is a, or bit random bitcoin mining with co public key private key bitcoin. How do we keep private keys safe? Top Articles. Copy Link. I have a money coming to me for investments. Third-party applications, such as the incredibly useful browser-based Bit Address Wallet Details tabcan be used to decrypt BIP keys. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? For each input, the user will have to provide verification he is allowed to spend that output by adding a signature. Figures ledger journal cryptocurrency crypto app exchange show various examples of paper wallets with security and backup features. We'll get back to you as soon as possible.
Bitcoin private keys storing Bitcoin. LTC Litecoin. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. Featured on Meta. Do not post your Bitcoin address unless someone explicitly asks you to. To mine a block it is "enough" to guess the nonce that results in a hash compatible with the current difficulty level. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. Running key-to-address-ecc-example. A private key stored in a wallet that is encrypted by a password might be secure, but that wallet needs to be backed up. Based on BIP, an HD wallet should use only one level-1 branch of the tree, with the index number identifying the structure and namespace of the rest of the tree by defining its purpose. I'm asking it because "if I can think of it" someone else is probably already trying it. Lonnie Best Lonnie Best 6. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. BIP defined a system of sequentially generating private keys for use in wallets.
Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. BCH Bitcoin Cash. Thank you for quick answering. Now that we have defined addition, we can define multiplication in the standard way that extends addition. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. Look at the lockee virus. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. In real life, do you give your keys to someone unknown? This seed phrase is not only memorable, but communicable good luck telling someone a private key over the phone and thus has a far greater usability to a person than a private key does by itself. The "link" to Bitcoin initially happens during block generation where a certain amount of Bitcoin is generated and sent to the miner's public address; this is merely a record in the blockchain. Some even have a little digital screen to verify your transactions. Due to the 1: That is why you need to take extra safety measures when dealing with these services.
Tim Delmastro is a multi-award winning filmmaker and journalist, having researched and documented subjects relating to Bitcoin and other current events in finance for over a decade. Good luck visualizing that. BTC Bitcoin. Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing you to store multiple copies to protect against fire, flood, or other natural disasters. Child private keys are indistinguishable from nondeterministic random keys. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. This process is fairly simple. If the amount exceeds what you want to spend, the remainder can be send back to one of the input address or even a new address of your wallet, so you basically send yourself the exceeding amount of Bitcoins.
