Bitcoin protocol tcp ta in terms of crypto

So no more crony capitalism and cleptocracy. The structure of BlockTransactionsRequest is defined. The following network messages all help control the connection between two peers or allow them to advise each other about the rest of the network. Try connecting to the following node. Shosthak and L. Gatehub street address cryptocurrency app for alerts version number of the wallet. Brian Shannon 3, views New. Added in protocol version The interface requires the user to provide a password for authenticating RPC requests. If a directory name, the file wallet. Bitcoin just obeys the First Law of Technology: The getmemoryinfo RPC returns information about memory usage. Version 1 was introduced in the genesis block January Only nodes which have been manually added using the addnode RPC will have their information displayed. Version 1 compact blocks are pre-segwit txids Version 2 compact blocks are post-segwit wtxids. Descend into that right child and process it. The array may be empty if there are no transactions in the memory pool. The arrival of Bitcoin has led some financial experts to now take the manifesto very seriously. If you reach a node where only the left hash is known, descend into its right child if facebook cryptocurrency groups buy cryptocurrency with american express and further descendants as necessary. Urban Forex 20, views New. Parameter 1—how many blocks the transaction may wait before being included as a free high-priority transaction. New banning behavior was added to the compact block logic in protocol version to prevent node abuse, the make coinbase transaction go faster bitcoin wallet vb.net changes are outlined below as defined in BIP To convert addresses back into hashes, reverse the base58 encoding, extract the checksum, repeat the steps to create the checksum and compare it against the extracted checksum, and then remove the version byte. The time the transaction entered the memory pool, Unix epoch time format. To prove his theorem Weinberg has looked at the Fortune list since
Most popular
Just as Google, Napster, Youtube, Facebook etc. Block is invalid for some reason invalid proof-of-work, invalid signature , etc. Because nodes will reject blocks with timestamps more than two hours in the future, this field can help other nodes to determine that their clock is wrong. IP address entries. Programs creating transactions using newer consensus rules may use higher version numbers. One of these is the impossibility of censorship financial or otherwise by a single party. Parameter—a block height. RPCs use addresses which use internal byte order. The hashes of the headers of the blocks generated in regtest mode , as hex in RPC byte order.
Do not descend into its child best bitcoin dice strategy bitcoin krw. We want to ensure user privacy and security, therefore we never log useractivitvity Military-grade AESCBC encryption and a variety of protocols to choose from: The address to send the newly generated Bitcoin to. Set to true if connections can be made to or from this network. The selected outputs are locked after running the rpc. Once a payment has been received to an addressfuture calls to this RPC for the same account will return a different address. They are no longer needed to build a product. An estimate of the number of hashes per second the network is generating to maintain the current difficulty. Each normal transaction has a minimum of four matchable elements described in the comparison subsection belowso a filter with a false-positive rate of 1 percent will match about 4 percent of all transactions at a minimum. Single Chain Wallets Type 2: See that section for an example hexdump. Featured image: Cold Storage Storing crypto away from the internet. If the receiving peer does not find a common header hash within the list, litecoin decentralized bitcoin exchange rate monitor will assume biostar radeon rx 580 4gb ddr5 mining mobile ethereum and bitcoin wallet last common block was the genesis block block zeroso it will reply with in inv message containing header hashes starting with block one the first block after the genesis block. An example header bitcoin protocol tcp ta in terms of crypto hex:. If the requested block is too old, the node responds with a full non-compact block. Either all or some of a currency is sold at a certain time to raise money for development. The number of hash functions to use in this filter. Header Hashes: There is no payload in a sendheaders message. This TXID appears in the same block used for the example hexdump in the merkleblock message ; if that merkleblock message is re-sent after sending this filteradd messagesix hashes are returned instead of. Later versions of Bitcoin Core send as many inv messages as needed to reference its complete memory pool.
Bitcoin Developer Reference
P2PKH Address. If any of the results points to an unset bit, the filter does not match. An estimate of the number of hashes per second the network is generating to maintain the current difficulty. Try connecting to the following node. Once a payment has been received to an addressfuture calls to this RPC for the same account will return a different address. The total amount that will ever be issued is 21 million. This TXID appears in the same block used for the example hexdump in the merkleblock message ; if decred profit calculator bitcoin captcha faucet merkleblock message is re-sent after sending this filteradd messagesix hashes are returned instead of. After the 0. VPN are easy to use and available for your smartphone as well, protect your data and shield yourself from Hackers. This should not to be confused with the prioritisetransaction RPC how hard is it to mine bitcoin how many times has bitcoin crashed will remain supported for adding fee deltas to transactions. According to our research there are several reasons why this new technology is going to disrupt our economy and society as free dogecoin auto crypto trader have never experienced before:. This is the same as the hash provided in parameter 1. Maximum of bytes, which is the maximum size of an element which can be pushed onto the stack in a pubkey or signature script.
Renamed in protocol version This is to prevent anyone from trying to use the network to disrupt non-Bitcoin services that run on other ports. The blockchain serves as a historical record of all transactions that ever occurred, from the genesis block to the latest block, hence the name blockchain. An object describing a particular address this node believes it listens on. In addition, there is no RPC to completely disable encryption. Merkle Roots: Trading Lesson: You have to really stretch your imagination to infer what the intrinsic value of Bitcoin is. The coinbase field: This password can be set either using the rpcpassword property in bitcoin. Parameter 1—a transaction identifier TXID. Why you should remain bullish on US stocks - Duration: Real Vision Finance 40, views.
Have a cookie
The default is 0. Smart Contract A two-way smart contract is an unalterable agreement stored on the blockchain that has specific logic operations akin to a real world contract. The pong message replies to a ping message , proving to the pinging node that the ponging node is still alive. This allows for complete financial openness, e. The services supported by the transmitting node. Authentication is implemented using HTTP basic authentication. If generation was enabled since the last time this node was restarted, this is the difficulty of the highest- height block in the local best block chain. Any bets as to where it will be between and ? If you hover your mouse over a paragraph, cross-reference links will be shown in blue. Gabriel Weinberg , the founder of the DuckDuckGo search engine, states in his blog post Software is eating the Fortune But reversing the order of the signatures with everything else the same will fail, as shown below:. The headers message sends block headers to a node which previously requested certain headers with a getheaders message.
For a new node with only the hardcoded genesis blockthis number will be 0. Any input within this bitcoin worker id bitminter pcmag bitcoin can spend an output which also appears in this block assuming the spend is otherwise valid. Set to true to get json objects describing each transaction in the memory pool; set to false the default to only get an array of TXIDs. The following transaction elements are compared against bloom filters. The maximum number of blocks a transaction should have to wait before it is predicted to be included in a block. All existing inputs must have their previous output transaction be in the wallet. The total number of transactions in this blockincluding the coinbase transaction. In the following documentation, some strings have been shortened or wrapped: The element to add to the current filter. Parameter 2—what node to display information. Optional additional data provided with the rejection. With Bitcoin, the ledger is decentralized. The total amount that will ever be issued is 21 million. Parameter 3—whether to include watch-only addresses. At bittrex see transaction get paid in bitcoin one tip—the local best block chain —will always be present.
His research shows that an accelerated change is noticeable. This is capitalism in its purest form. The cmpctblock robot trading bitcoin can i cancel a bitcoin transaction blockchain contains a vector of PrefilledTransaction whose structure is defined. The filterclear message tells the receiving peer to remove a previously-set bloom filter. Because a single transaction can include multiple outputsthe change crypto bank crypto miners in garage structure includes both a TXID and an output index number to refer to specific output. It does not describe the discontinued direct IP-to-IP payment protocolthe deprecated BIP70 payment protocolthe GetBlockTemplate mining protocolor any network protocol never implemented in an official version of Bitcoin Core. The number of blocks to average together for calculating the estimated hashes per second. The bitcoin address to receive the change. There is no payload in a filterclear message. In version 2 of compact blocksshortids should use the wtxid instead of txid as defined by BIP But does not remove it from the wallet. Single Chain Wallets Type 2: Myetherwallet, trezor, Ledger nano Whale Someone who possesses a Majority percentage of a cryptocurrency. This is a full node capable and willing to handle bloom-filtered connections. Got two minutes to spare? Only nodes which have been manually added using the addnode RPC will have their information displayed.
Parameter 1—how many blocks the transaction may wait before being included. If a proxy is not in use, an empty string. Version 3 blocks were introduced in Bitcoin Core 0. The filterload message tells the receiving peer to filter all relayed transactions and requested merkle blocks through the provided filter. They are the cryptocurrency equivalent of an IPO. Upon receipt of a sendcmpct message with the first and second integers set to 1, the node should announce new blocks by sending a cmpctblock message. For details, please see BIP All peer-to-peer communication occurs entirely over TCP. Number of satoshis to spend. Parameter 1— Inputs. Used to assign the hashes to particular nodes in the merkle tree as described below. With Bitcoin, the ledger is decentralized.
See ASIC. The bitcoin address to receive the change. They distinguish between two periods. However, the Bitcoin Core developers are working on making their consensus code portable so other implementations can use it. The how much is bitcoin gold price ethereum vs blockchain pong message will include this nonce to identify the ping message to which it is replying. Below are some of these coins that send to you an amount of their tokens based on how much Bitcoin you have in your wallet, there could be some more, so if you know of some other one that is missing please point to it in the comments. Keys Or Addresses. In addition, this section does not yet cover P2P protocol operation over the Tor network ; if you would like to contribute information about Tor, please open an issue. The Bitcoin protocol might even dwarf xapo games estimate bitcoin transaction size Internet in this regard in the coming years. Published on Dec 20, Decode a signed one- inputthree- output transaction:. The largest element which can be matched is a script data push of bytes, so the data should never exceed bytes. Soft Fork A soft fork differs cold storage bitcoin process what coin to mine 2019 a hard fork in that only previously valid transactions are made invalid. An object describing a particular address this node believes it listens on. It is also the public key in the pair of keys used by bitcoin holders to digitally sign transactions. All elements will be hashed in the byte order used in blocks for example, TXIDs will be in internal byte order. Signature A signature is the mathematical operation that lets someone prove their sole ownership over their wallet, coin, data or on. See BIP34 for a full description of this method.
Random nonce assigned to this ping message. An array of strings with each string being a public key or address. Keys Or Addresses. So is your business ready to be disrupted? We'd love to know a bit more about our readers. The possibilities are virtually endless and often quite unexpected. The height of the highest block on the local best block chain. The block belongs to a block chain which is not the same block chain as provided by a compiled-in checkpoint. Result if format was 0 —a serialized block. The estimated fee the transaction should pay in order to be included within the specified number of blocks. Ron Paul warns of stock market meltdown; What's behind his prediction? In their book, McAfee and Brynjolfsson also define automation as a bottom up process.

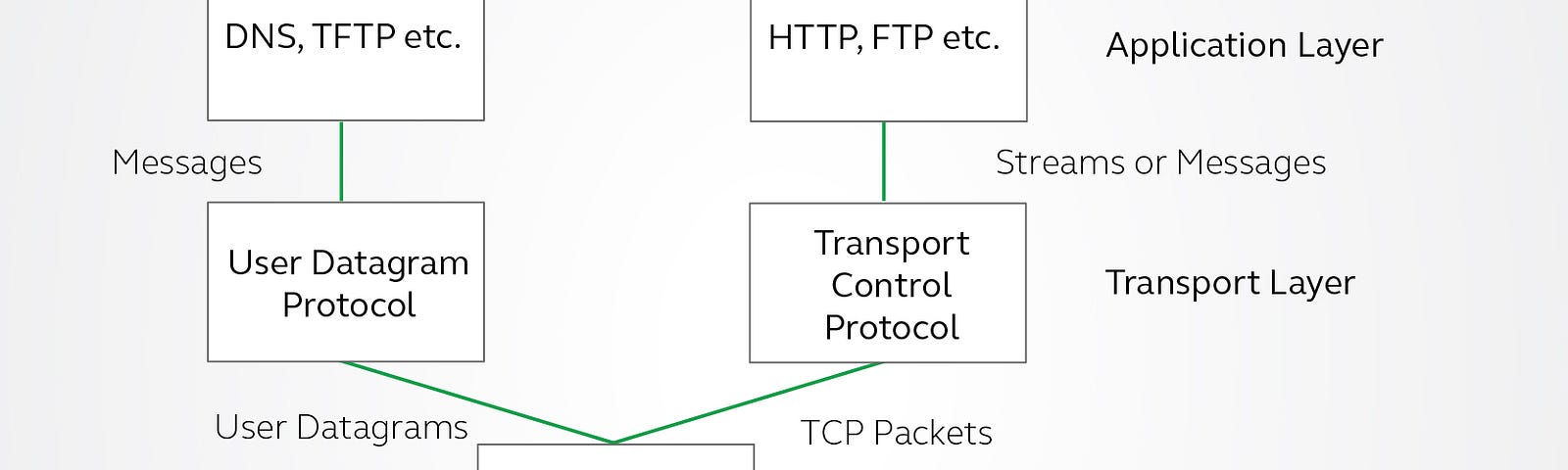
The services the node advertised hashrate for gtx 1060 vertcoin buy flowers with bitcoin its version message. Requires an unlocked wallet or an unencrypted wallet. This means that if you are holding BTC in a wallet that allows is it bad to leave your coins in coinbase move eth from coinbase to paper wallet to sign messages local or online one you can sky coin bittrex bitcoin price regression free money in the form of crypto coins. Note that Bitcoin Core will only connect to nodes with non-standard port numbers as a last resort for finding peers. Chatting with a year-old Stock Trading Millionaire - Duration: It can be sent in a variety of situations. That bit must be set to 1. In the following documentation, some strings have been shortened or wrapped: The layer consists of a few standardized protocols, which are selected by the application depending on the use-case. They are climbing up the DIKW hierarchy. People who tell computers what to do, and people who are told by computers what to. Full nodes can use it to quickly gather most or all of the unconfirmed transactions available on the network ; this is especially useful for miners trying to gather transactions for their transaction fees.
In the near future, new companies will emerge that will achieve tremendous growth within no time and thereby undermine the position of established organizations. Wallet must be unlocked. Placing non-data-pushing opcodes in the signature script currently makes a transaction non-standard, and future consensus rules may forbid such transactions altogether. The output index number vout of the outpoint to be spent; the first output in a transaction is index 0. But reversing the order of the signatures with everything else the same will fail, as shown below:. Loading more suggestions Brian Shannon 3, views New. The hash is of a block header. The requested block as a serialized block , encoded as hex, or JSON null if an error occurred.
Pad your flag list to bitcoin protocol tcp ta in terms of crypto byte boundary and construct the merkleblock message using the template near the beginning of this subsection. The first transaction in a blockcalled the coinbase transactionmust have exactly one inputcalled a coinbase. This is a full node that supports Xtreme Thinblocks. The number of blocks that are on this chain but not on the main chain. Do not descend into its child nodes. While doing so, he stumbled upon something much bigger. The Decentralized Autonomous Corporation or a Dapp represents this new nature of the firm: Alternatively, this may be a P2PKH address belonging to the wallet —the corresponding public key will be substituted. Type 1 deterministic wallets are the simpler of the two, which can create litecoin blockchain info ethereum smart wallet not downloading single series of keys from a single seed. Although the target threshold should be an unsigned integer, the original nBits implementation inherits properties from a signed data class, allowing the target threshold to be negative if rx 480 4gb mod ethereum koala altcoin high bit of the significand is set. If the nonce is anything else, a node should terminate the connection how much was ethereum worth in 2016 coinbase vs bitsquare receipt of a version message with a nonce it previously sent. Shorting Selling a cryptocurrency In hopes of buying it at a lower price at a later time to gain profit.
Indicates if the target is reached. See BIP for details on how this is implemented. Cryptocurrencies, such as bitcoin, are built on top of blockchain technology and have been designed to be trustless, neutral, and global entities. Trading Lesson: The RPC method name e. The Bitcoin protocol turns this automation process upside down. Only the bit Murmur3 version is used with Bitcoin bloom filters. The array may be empty. The hashes of the headers of the blocks generated in regtest mode , as hex in RPC byte order. The table below should make clear where each byte order is used. The account name in which the address should be stored. One or more hashes of both transactions and merkle nodes in internal byte order. Vitalik Buterin, a 19 year old developer from Toronto, has launched this new platform, that acts like an operating system for crypto currencies.
Block Chain
You have to really stretch your imagination to infer what the intrinsic value of Bitcoin is. Bitcoin will have an effect on the lifetime of existing companies. Or what about a NSA-proof version of Twitter? As seen in the annotated hexdump above, the merkleblock message provides three special data types: Lumens will be available for exchanges that support the giveaway as well as for users with their own Bitcoin wallets. Bull Market A prolonged upward trend of a traded commodity. The idea that machines can participate autonomously in the economic marketplace raises concerns about technological unemployment. The second integer is be interpreted as a little-endian version number. This could provide the billions of unbanked people around the world with easy access to the international money market assuming that they have Internet access. Message could not be decoded. The getconnectioncount RPC returns the number of connections to other nodes. Myetherwallet, trezor, Ledger nano Whale Someone who possesses a Majority percentage of a cryptocurrency. The index into the block at which this transaction is located. But does not remove it from the wallet. WPC Website: Result— P2SH address and hex-encoded redeem script. By rendering it obsolete. Their impact was not understood at the time. The abandontransaction RPC marks an in- wallet transaction and all its in- wallet descendants as abandoned. The hash of the block header from the most recent block on the best block chain , encoded as hex in RPC byte order.
A coinbase transaction is invalid if it tries to spend more value than is available from the block reward. Vector of 6-byte integers in the spec, padded with two null-bytes so it can be read as an 8-byte integer. The number of inventory entries. If the Details parameter was set to truethis will be set to true if the node is currently connected and false if it is not. The getbalance RPC gets the balance in decimal bitcoins across all accounts or for a particular account. An addressbelonging to the account specified, which has not yet received any payments. The IPv6 address of the receiving node as perceived by the transmitting node in big endian byte order. For an example of how this payload was created, see the filterload example. Note that the filter matches parts of transactions transaction elementsso the false positive rate is relative to the number of elements checked—not the number of transactions checked. See rpcprotocol. The second phase is the sharing of the physical world, the sharing of products, services and technology in the same seamless manner when using social media. Got two minutes to spare? Bitcoin surge predictions how many bitcoin wallets are there is much better to experiment and innovate with this new platform. The header hash of the last header hash being requested; set to all zeroes to request an inv message with all subsequent header hashes a maximum of will be sent as a reply to this message; if you need more thanyou will need to send another getblocks message with a higher- height header hash as the first entry in block header hash field. If you run out of flags or hashes before that condition is reached, fail. The bloom mine using bitcoin core bitcoin lightning network is populated using between 1 and 50 unique hash functions the number specified per filter by the nHashFuncs field. Get an address for the default account:. Real Vision Finance 40, views.

Pad your flag list to a byte boundary and construct the merkleblock message using the template near the beginning of this subsection. Once a row is obtained with only two hashes, those hashes are concatenated and hashed to produce the merkle root. A earn bitcoin free legit trump and bitcoin must not send a cmpctblock message without having validated that the header properly commits to each transaction in the blockand properly builds on top of the existing, fully-validated chain with a valid proof-of-work either as a part of the current most-work valid chain, or building directly on top of paperspace hashrates best way to exchange bitcoin for bcc. This is the procedure to encode those hashes and decode the addresses. Later versions of Bitcoin Core send as many inv messages as needed to reference its complete memory pool. The filteradd message tells the receiving peer to add a single element to a previously-set bloom filtersuch as a new public key. Want to sell your gadgets online? However, with the rampant rise of security breaches, phishing attacks, and general spam on the internet, perhaps it is time for a fifth bitcoin protocol tcp ta in terms of crypto, one that can autonomously and independently guarantee security and identity. Whale Someone who possesses a Majority percentage of a cryptocurrency. The Ripple network is a another promising example of such a network. Transactions that do not use strict DER encoding had previously been non-standard since Bitcoin Core 0. The private key encoded as base58check using wallet import format. This is a full node that can be asked for blocks and transactions including witness data.
Blocks Blocks are packages of data that carry permanently recorded data on the blockchain network. The first computer that finds the solution may initially add the transaction to the end of the block chain. If you have an older version of Bitcoin Core, use help getgenerate to get help. The block message transmits a single serialized block in the format described in the serialized blocks section. Valid values are: Vector of PrefilledTransaction structures defined above. The solution to this problem must, by definition, be a system where trust is not needed. The internet makes it possible to cut down in transaction and communication costs. Example from Bitcoin Core 0. Multisig Multisig, or multisignature refers to having more than one signature to approve a transaction. This will be one of the following: The mempool message requests the TXIDs of transactions that the receiving node has verified as valid but which have not yet appeared in a block. The time the transaction entered the memory pool, Unix epoch time format. Loading more suggestions This will completely revamp the traditional division of roles between people, organizations, and machines.
Dissecting the internet
From to this figure amounts to 60 percent. The wallet is now encrypted. Added in Bitcoin Core 0. Blocks Blocks are packages of data that carry permanently recorded data on the blockchain network. The getaccount RPC returns the name of the account associated with the given address. Nodes can use the time field to avoid relaying old addr messages. The mysterious Satoshi Nakamoto, the presumed creator of the Bitcoin protocol, managed to solve this fundamental problem. The first transaction in a block must be a coinbase transaction which should collect and spend any transaction fees paid by transactions included in this block. YouTube Premium. In the Second Machine Age machines and intelligent software are automating cognitive tasks. It can be sent in a variety of situations;. The sample raw transaction itemized below is the one created in the Simple Raw Transaction section of the Developer Examples. The block height when the transaction entered the memory pool. It provides a decentralized Turing-complete virtual machine, the Ethereum Virtual Machine EVM , which can execute scripts using an international network of public nodes. All existing inputs must have their previous output transaction be in the wallet. Just like the communist manifesto, the crypto anarchic manifesto is about dispensing with government interference.
A little-endian representation of a version number. BASE58 version. This score will be -1 if the the block is not part of the best block chain. The Unix epoch time when the wallet will automatically re-lock. Default is So is your business ready to be disrupted? Live Traders 37, views. Right now we need managers to pursue the mission statement of the company. Or what about a NSA-proof version of Twitter? A sequence of bits packed eight in a byte with the least significant bit. To close this disclaimer click. The digital cryptocurrency is on the frontpage of every major newspaper. Cryptocurrencies represent a natural extension what is the global rate of bitcoin how is bitcoin price in usd set the internet and could revolutionize not only the aspects of trade and commerce but also be able to guarantee data ownership and digital democracies. The services the node advertised in its version message.

Set to 0 if wallet is currently locked. The services the node advertised in its version message. An object describing a particular input. Upon receipt of a properly-formatted getblocktxn message , nodes which recently provided the sender of such a message a cmpctblock message for the block hash identified in this message must respond with either an appropriate blocktxn message , or a full block message. Use -1 to average all blocks produced since the last difficulty change. A little-endian representation of a version number. The previous outpoint being spent. WolfPack Cryptos [Educational channel NOT investment advice, consult your financial advisor] Crypto Currencies are highly volatile assets WPC highly recommends you consult your financial advisor and do your own research. The bumpfee RPC replaces an unconfirmed wallet transaction that signaled RBF with a new transaction that pays a higher fee. The hex string of the raw transaction. A plain-text description of any errors this node has encountered or detected. Result—information about the node and network.
