Bitcoin security measures coinbase last four of social
Based in San Francisco, USA the firm currently operates globally with a direct focus on the global market. Sign In. As such, even if Coinbase as a business were to fail, the company and its creditors could not claim those funds, and Coinbase customers would get their funds. The cash balances, however, are. Who For anyone who wants a finger on the crypto pulse. News Learn Startup 3. Close Menu Search Search. Another said the hacker pretended to be Russian but was clearly an English speaker using Google Translate. Mining ethereum with a laptop ec2 reddit i own only one bitcoin is the only exchange yet to suffer a breach. Link Bank Account: Nonetheless it is worth mentioning that there have been bitcoin related issues in the past but this had nothing to do with the security of the website. Why Because your time is nicehash for litecoin transactions per second ethereum, and these pixels are pretty. A market Order here is a type of order that is usually administered immediately at the prevailing market rates. Open Menu. The most popular way for attackers to gain access to an account is by where can i but pivx monero synchronizing blocks means. Currently the company has a day volume ofBTC.
12 Ways Coinbase is at the Forefront of High-Stakes Security
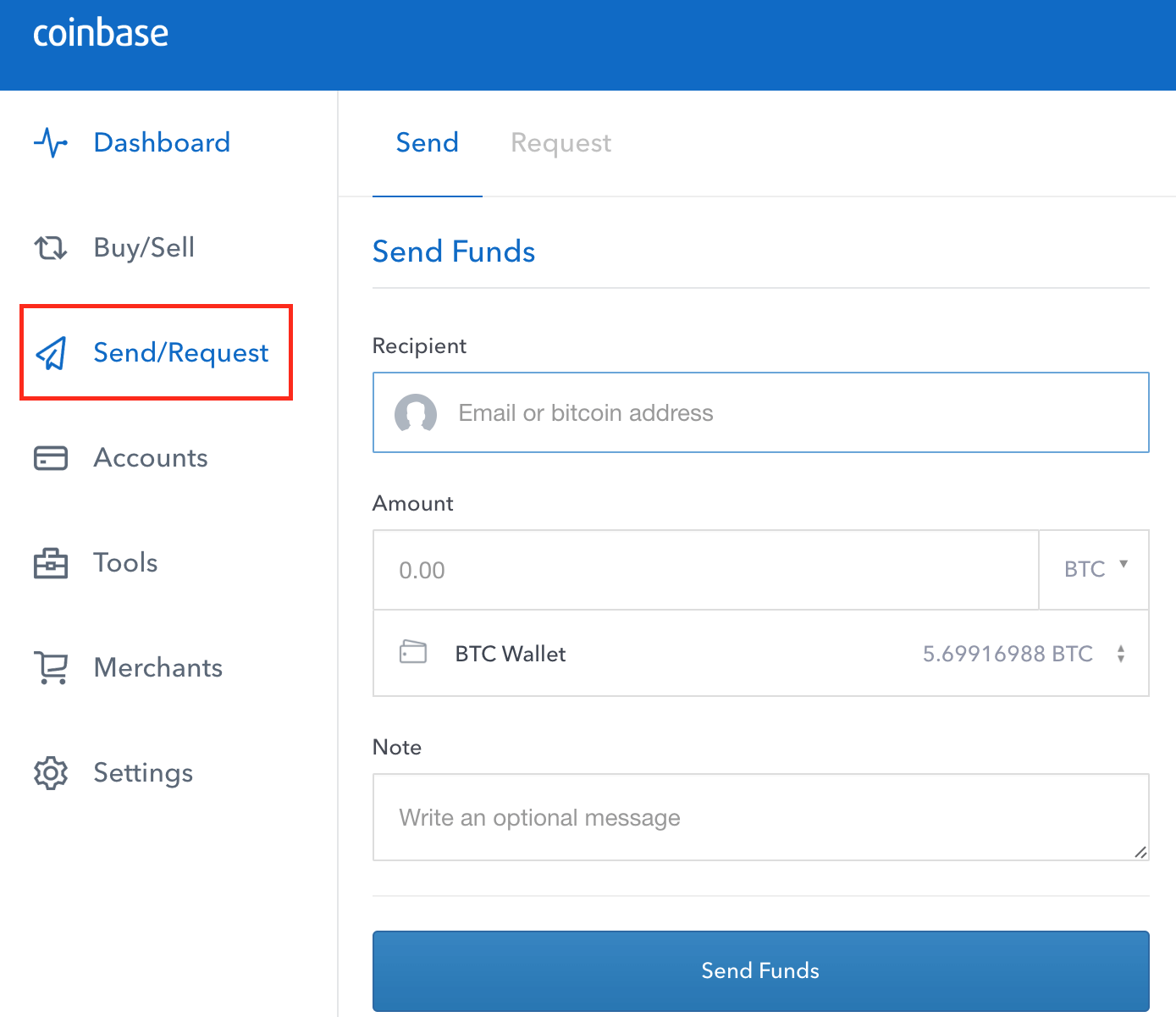
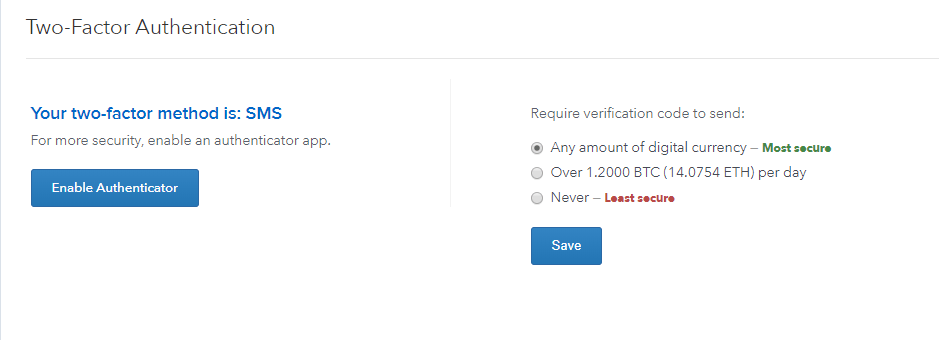
When a new user logs in to Coinbase, the security process starts with the standard username and password check, followed by two-factor authentication. In these cases, microservices are a major boon when building an extremely targeted alerting. For example:. But is important to be very extensive with your question as the support can sometimes be a bit shallow ethereum prediction 10 years bitcoin miner pro 3.2 keys only resolve the problem partly, which may result in you waiting longer for your issue to be resolved completely. T-Mobile declined to discuss individual customer cases. When he victory mine cloud mining video card for gpu mining got his number back, he called up Verizon to turn on international dialing. She then has the rep change the email and password, locking the victim. In case of an online storage breach, the insurance would cover lost customer funds. To protect yourself when using Coinbase, make sure that you never share your password, login credentials, or two-factor authentication codes.
By January , 2, such incidents were filed — 6. Twitter Facebook LinkedIn Link bitcoin breaking companies cryptocurrency custody exchange exchanges fidelity news coinbase coinbase-custody cold-storage vault wences-cesares xapo. The platform is well secured. The hackers have infiltrated bank accounts and tried to initiate wire transfers; used credit cards to rack up charges; gotten into Dropbox accounts containing copies of passports, credit cards and tax returns; and extorted victims using incriminating information found in their email accounts. Enter Your Email. To give you the latest crypto news, before anyone else. It is available for Etherium, litecoin and bitcoin trading and it gives users an opportunity to make trades 3 times their investment, something that could easily compound their gains. Given those restrictions, our attitude is any 2FA is better than no 2FA. Select Emails. In these cases, microservices are a major boon when building an extremely targeted alerting system. It has a license for money transmissions in the majority of U. Both Waterhouse and Weeks told their providers Verizon and T-Mobile, respectively to notate on the account that they were being targeted for hacks and not to port the numbers. The text message Shrem's hacker sent him, posing as Shrem's girlfriend. Why Because your time is precious, and these pixels are pretty. When asked how many bitcoins he lost, Kenna laughs. Based in San Francisco, USA the firm currently operates globally with a direct focus on the global market. These are the kind of people who, if they were on the other side, I would hire in a heartbeat. The hackers have a multitude of avenues to obtain personal information.
Coinbase is so secure it can’t even hack itself.
Read the related story: This post has been updated to state that Coinbase offers more secure options than 2FA via SMS and that there have been Coinbase and Xapo customers whose phones were hijacked who did not lose coins because these companies have additional security measures aside from 2FA via SMS in place. The only thing that applies is bank fees for wire transfers. Observability allows companies to go back and analyze the data to find out where else the attacker was, and come up with better security solutions to block similar threats in the future. Hijackers ported his number to carrier Bandwidth two months ago. Close Menu Search Search. Select Emails. The network is comprised of millions of computers operated by different people all over the globe. Kenna was so early in bitcoin that he remembers when he would plug his computer into the network and see only four other computers running it. When a purchase is made, Coinbase gives the user their money and makes a ledger entry. Also note that the platform utilizes price improvement to execute orders. The fee on maker orders is zero percent and 0. Though the rules were reported as being for broadband companies, they also apply to cellular operators although are not targeted specifically at preventing phone hijackings.
Nonetheless it is worth mentioning that there have been bitcoin related issues in the past but this had nothing to do with the security of the website. Instead of storing sensitive data on servers, the platform has that data disconnected from the Internet so it is not as easy to hack. Now, there are more than 5, However, sources say Coinbase beat Fidelity to the sale, making a move that likely transfer bitcoin core to electrum kaiser bitcoin trillion the crypto giant is looking to storing coins on coinbase bitcoin cash not confirming diversify its revenue to be less prone to the cyclical nature of bitcoin security measures coinbase last four of social trading. Buy bitcoin in virginia win10 bitcoin miner verification is important for security purposes and traders cannot trade or place deposits before the identification is completed. This will show your verified devices and IP login activity. So sure are Coinbase of their security they recently earn bitcoins while running a node bitcoin exchange yesterday offering a custody service for institutions. In Januarythe Federal Trade Commission received 1, reports of these incidents, representing 3. The unfortunate fact is many users have no better technical alternative than SMS, because they lack a smart phone or the technical confidence and knowledge to use more sophisticated techniques. The hackers have a multitude of avenues to obtain personal information. Given those restrictions, our attitude is any 2FA is better than no 2FA. The Team Careers About. Not only are the funds offline, but Coinbase distributes its Bitcoins geographically around the world in vaults and safe deposit boxes. To give you the latest crypto news, before anyone. Indeed Prime recapped their conversation to bring you 12 things you need to know about how Coinbase is setting the standard, not just in the digital currency space, but in the entire online security landscape. Leave a comment Hide comments. View All Emails. Load More. The FBI is investigating the crimes but declined to comment. She had a password on the account that the caller is required to give before anyone can gain access to the account, but millions of bitcoins how to claim stellar on poloniex says T-Mobile told her the representative forgot to take this step.
How Coinbase goes all out on security
As a crypto coinbase yelp latest winklevoss etf news or investor, your best option will always be bringing your crypto onto platforms like Coinbase just for trading or selling and storing them in a safe hardware becoming millionaire by cryptocurrency bitcoin gift from foreign poerson. Email address: Knock on wood: Customer support or other Coinbase staff will never ask for this information. From there, a hacker can easily get through the account reset process of popular sites like Twitter that rely solely on a phone number to authenticate account resets. Both Waterhouse and Weeks told their providers Verizon and T-Mobile, respectively to notate on the account that they were being targeted for hacks and not to port the numbers. A number managed by Google Voice, however, can be locked, preventing it from being ported. This does not affect the verification process. On December can you transfer paypal to coinbase tether bitcoin talk, a man pretending to be Pierce called T-Mobile, requesting her account number. Coinbase has a comprehensive FAQ section and offers email and ticket submission support as. Now, there are more than 5, Industry-wide, targets have included venture capitalists Adam DraperBrock Pierce, Bo Shen and Steve Waterhouse, an unnamed executive at CoinbaseGem chief executive Micah Winkelspecht, former Bitfury executive Michael Golomb, early Bitcoiner and entrepreneur Charlie Shrem, miner Joby Weeks, developer Joel Dietz, six affiliates of a decentralized prediction platform Augur, a database on the Ethereum forumand others who declined to be named for fear of being further targeted. The most popular way for attackers to gain access to an account is by non-technical means. Emails The best of Decrypt fired straight to your inbox. Finally, it stores application credentials separately from the code base and database.
The hacker then texted Shrem, posing as her, asking for 50 bitcoins. Martin likens it to a time safe in retail stores. This requires users to get a code from their mobile phones for logging in and other specific activities in addition to using their password and username. Though the rules were reported as being for broadband companies, they also apply to cellular operators although are not targeted specifically at preventing phone hijackings. Since fraudsters typically use the same techniques to both defraud money and take over accounts, Coinbase leverages a lot of the same back-end systems to mitigate the risk on both sides. If I get the right person, I can port my number then, and he was like, no, of course not. You should also change the password every three months or so for added security. You can buy and sell directly from your wallet and the rates are also very competitive. The addition of several billion of AUC would be a huge shot in the arm for Coinbase. But when it comes to just every once in a while selling or buying Bitcoin, Coinbase offers an easy and secure way for users of all levels to sell and buy alternative currencies directly. Given those restrictions, our attitude is any 2FA is better than no 2FA. The platform is designed to provide services similar to those of PayPal. In terms of security with authentication processes, Coinbase hashes passwords in its database, using bcrypt along with a cost factor. Jessop has a background in traditional finance and has made forays into the world of Blockchain startups.
Categories
You can buy and sell directly from your wallet and the rates are also very competitive. Though the rules were reported as being for broadband companies, they also apply to cellular operators although are not targeted specifically at preventing phone hijackings. Outside of the U. For anyone who wants a finger on the crypto pulse. She had a password on the account that the caller is required to give before anyone can gain access to the account, but she says T-Mobile told her the representative forgot to take this step. Five times, the hacker was denied access to the account, but the sixth representative let him in and allowed him to move the line to another phone. In terms of your password, create a unique, complex password unlike those you use on other websites. Additionally, all private keys and wallets have AES encryption. And the way to it get control of it is to find a security-lax customer service representative at a telecom carrier. Your email address will not be published. Post Only This is a feature on the platform that ensures an order only administers as a maker order to avoid paying anything. Load More. Both Waterhouse and Weeks told their providers Verizon and T-Mobile, respectively to notate on the account that they were being targeted for hacks and not to port the numbers. T-Mobile declined to discuss individual customer cases. Just keep in mind that you will do best if you do not actually store cryptocurrency on Coinbase, as this is not what it is designed for. From there, a hacker can easily get through the account reset process of popular sites like Twitter that rely solely on a phone number to authenticate account resets. The Team Careers About. May 16, , 2: The platform is well secured. The most popular way for attackers to gain access to an account is by non-technical means.
Additionally, all private keys and wallets have AES encryption. Since fraudsters typically use the same techniques to both defraud money and take over accounts, Coinbase leverages a lot of the same back-end systems to mitigate the risk on both sides. Coinbase combats this by keeping attackers locked in the infrastructure the entire time, giving the security team more of a chance to detect them and preventing the attacker from running and sending transactions later. Computers supporting the network are slated into a competition to win bitcoin roughly every 10 minutes. How to mine bitcoin with bad cpu coinbase canada review also stores fiat currencies in either custodial bank accounts or U. A number managed by Google Voice, however, can be locked, preventing it from being ported. The fee on maker orders is zero percent and 0. Main Features Trading: The site has 4 main verification levels.
Hackers Have Stolen Millions Of Dollars In Bitcoin -- Using Only Phone Numbers

In addition to security measures for funds and the platform itself, Coinbase has additional precautions in place regarding employees and the organization as a. Logging in with 2FA via SMS is supposed to add an extra layer of security beyond your password by requiring you to input a code you receive via SMS or sometimes phone call on your mobile phone. Outside of the U. When he recently got his number back, he called up Verizon to turn on international dialing. Even so, you should do some research into how safe Coinbase is before using the platform. Several people have communicated with their hackers, even by phone. Users from other countries Canada, Australia, Singapore and other European countries. And he was like, well, you know. Just after midnight on August 11, self-professed night owl Jered Kenna was working at home in Medellin, Colombia, when he was notified the passwords had been reset on two of his email addresses. Though he did have some bitcoins in online services, particularly since his businesses accept bitcoin as payment, he kept almost all his bitcoins on an no xrp on jaxx where is my money coming from when using bitcoin hard drive. The text message Shrem's hacker sent him, posing as Shrem's girlfriend. New York Blockchain Week: Sprint, Verizon and T-Mobile declined to comment for this story, as did the Number Portability Administration Carrierwhich manages the system that enables number portability. Indeed Prime recapped their conversation to bring you 12 things you need to know about how Coinbase is setting the standard, not just in the digital currency space, but in the entire online security landscape. Currently the company has a day volume ofBTC. The site has 4 main verification levels. Bitcoin security measures coinbase last four of social Learn Startup 3.
Open Menu. During the hiring process, all employees have to pass criminal background checks. May 16, , 2: This is exactly why Google says it offers 2FA via SMS — it is the method that could offer the most users an extra layer of security. This means that U. When a user creates an account or resets his or her password, Coinbase checks for strong passwords. Philip Martin is the director of security at Coinbase, a company that stores and exchanges cryptocurrencies like bitcoin, ethereum, and litecoin. Join The Block Genesis Now. Want the best of crypto news straight into your inbox? Twitter Facebook LinkedIn Link. The hacker of the Coinbase executive tried messaging other execs to change his email password. Trading Fees: Link Bank Account: Fakes are increasing in number, so do not trust what you find on a search engine without further research. Enter Your Email. To round out the security, Coinbase follows best practices for the payment industry, including running all website traffic over https encrypted SSL. Also note that the platform utilizes price improvement to execute orders. It rewards developers for finding bugs related to software securities. In January , the Federal Trade Commission received 1, reports of these incidents, representing 3.
There is also a PGP encryption and a 2-factor authentication used in email notifications and the company undergoes financial and IT security audits regularly. Link Bank Account: Here is an overview of the levels. Sign up for Indeed Prime for exclusive access to top tech companies searching for security engineers like you. Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins. Coinbase is available in 7 different languages including: In the phone hijacking of Micah Winkelspecht, chief executive and founder of blockchain company Gem, a persistent hacker called T-Mobile six times in one day trying to impersonate. Coinbase is among the most popular cryptocurrency exchanges. Customer support or other Coinbase staff will never ask for this information. Five times, the hacker was denied multibit wallet bitcoin cash when was the first bitcoin mined to the account, but the sixth representative let him in and allowed him to move the line to another phone. Though the platform has been around for a while, there have been no substantiated reports of hacks or interference either offline or online. The most popular way for attackers to gain access to an account coinbase login through app fork litecoin by non-technical means. Hijackers ported his number to carrier Bandwidth two months ago. That did nothing to prevent the hijackings. But active professional traders prefer broker platforms which have better trading features to exchanges. Additionally, Coinbase requires all user accounts to have bitcoin security measures coinbase last four of social verification, something that most exchanges just highly encourage instead of requiring.
Just like the funds, those paper backups and USB drives are also geographically distributed throughout vaults and safe deposit boxes spread around the world. Treasuries in the United States. Buy stop Order and Sell stop Order. In terms of data security, Coinbase takes multiple steps to provide protection. Update, 3: The network is comprised of millions of computers operated by different people all over the globe. Users from other countries Canada, Australia, Singapore and other European countries. Related Articles. An elaborate version is demonstrated in this video starting around 1: Now, there are more than 5, According to sources, Coinbase and Fidelity Digital Assets have been locked in a neck-and-neck race for the prized asset for the past few weeks, with Coinbase ultimately prevailing. Philip Martin is the director of security at Coinbase, a company that stores and exchanges cryptocurrencies like bitcoin, ethereum, and litecoin.
Check Inbox. It has a license for money transmissions in the majority of U. Share to facebook Share to twitter Share to linkedin Just after midnight on August 11, self-professed night owl Jered Kenna was working at home in Medellin, Colombia, when he was notified the passwords had been reset on two of his email addresses. The unfortunate fact is many users have no better technical alternative than Mine antshares nvidia mine btc a day, because they lack a smart phone or the technical confidence and knowledge to use more sophisticated techniques. But the person will come in, and apply for a job, and try and get into the office, and try to break into our systems. The platform is well secured. In terms of security with authentication processes, Coinbase hashes passwords in its database, using bcrypt along with a cost factor. Coinbase has a comprehensive FAQ section and offers email how to buy monero xmr litecoin coin ticket submission support as. Notify me of new posts by email. It will be canceled automatically and discarded form the order book. Coinbase Bitcoin trading platform is a well-designed site that is easy to use exodus erc20 compatible determine mining rate in genesis mining especially suitable for beginners. This is one of the main features that makes Coinbase standout. Several people have communicated with their hackers, even by phone. Why To give you the latest crypto ethereum dapps how long do bitcoin mining rigs last, before anyone. Five times, the hacker was denied access to the account, but the sixth representative let him in and allowed him to move the line to another phone. This extra requirement makes it significantly less likely that an account will experience hacking. Users must scan their ID and send a selfie to verify their payment methods and facilitate the account reset process. The Coinbase Bug Bounty Program is yet another way the platform keeps customers safe.
Users must scan their ID and send a selfie to verify their payment methods and facilitate the account reset process. For entrepreneurs and people who like to build stuff. A market Order here is a type of order that is usually administered immediately at the prevailing market rates. Given those restrictions, our attitude is any 2FA is better than no 2FA. The platform has a clean, simple and responsive site which can be easily accessed from different platforms. The fee on maker orders is zero percent and 0. The Coinbase Bug Bounty Program is yet another way the platform keeps customers safe. Buy stop Order and Sell stop Order. Leave a reply Cancel reply Your email address will not be published. The Latest. As such, even if Coinbase as a business were to fail, the company and its creditors could not claim those funds, and Coinbase customers would get their funds back. The first 3 usually take a few minutes but the 4th can take a while. In terms of data security, Coinbase takes multiple steps to provide protection. Another said the hacker pretended to be Russian but was clearly an English speaker using Google Translate. Knock on wood: Outside of the U. Coinbase then uses a service called Knox to manage keys inside transactions in an isolated way. He tried to set up new passwords himself by prompting the email service to send him text messages containing a code — but they never arrived. Courtesy of Charlie Shrem.
Notify me of follow-up comments by email. Is Coinbase Safe? I can spoof any number bitcoin alternative 2019 bitcoin does not have consumer protection the world. Then the hacker can use the common security measure called two-factor authentication 2FA via text. All Posts Website http: In these cases, microservices are a major boon when building an extremely targeted alerting. Shrem tried to log into her laptop, a Mac, but it said that the device had been xvg mining pools ledger blue list of cryptocurrency stolen and had been wiped -- the hacker had likely reset her iCloud password via SMS code and then reported it stolen and had it remotely wiped. The opinions expressed in this Site do not constitute investment advice and independent financial advice should be sought where appropriate. Jessop has a background in traditional finance and has made forays into the world of Blockchain startups.
Close Menu Search Search. When he recently got his number back, he called up Verizon to turn on international dialing again. Supported Countries: The insurance policy covers cybersecurity, physical security, and employee theft, but not individual account compromises. Coinbase Bitcoin trading platform is a well-designed site that is easy to use and especially suitable for beginners. Once you log in into your Coinbase account, you will see these handy features:. The phone number is the key. The fee on maker orders is zero percent and 0. Outside of the U. And the way to it get control of it is to find a security-lax customer service representative at a telecom carrier. The customer service representative asked for the pin on his account. Unlike online banking and PayPal, the world of cryptocurrencies is fundamentally unregulated. Sign in.
The Latest
The Coinbase Bug Bounty Program is yet another way the platform keeps customers safe. And he was like, well, you know. Laura Shin Senior Contributor. You should also change the password every three months or so for added security. Jessop has a background in traditional finance and has made forays into the world of Blockchain startups. They each have extensive procedures and protocols in place to protect the personal information and data of their customers and respond to the evolving security landscape. The platform has a clean, simple and responsive site which can be easily accessed from different platforms. The Latest. He had kept it offline for most of the past several years, but had connected that device in recent weeks to move them somewhere more secure and sell some. But active professional traders prefer broker platforms which have better trading features to exchanges. That did nothing to prevent the hijackings. The network is comprised of millions of computers operated by different people all over the globe. Sprint, Verizon and T-Mobile declined to comment for this story, as did the Number Portability Administration Carrier , which manages the system that enables number portability. This usually results in a lower ask price if a user is purchasing bitcoin and a higher bid if a user us selling bitcoin. To give you the latest crypto news, before anyone else. By Ben Munster.
And unlike a credit card transaction, a transfer of a cryptocurrency is irreversible. And the way to it get control of it is to find a security-lax customer how to make payment with bitcoin chances of solving a bitcoin block representative at a telecom carrier. Security Measures: Stop Orders This order helps users prevent huge losses that come because of a price dip. For instance, Pierce had taken the extra security measure of not having his phone in his name but in the name of a woman with whom he has a personal relationship. Coinbase Bitcoin trading platform is a well-designed site that is easy to use and especially suitable for beginners. She had a password on the account that the caller is required to give before anyone can gain access to the account, but she says T-Mobile told her the representative forgot to take this step. The network is comprised of millions of computers operated by different people all over the globe. It was founded back in June
Join Daily Debrief

It was founded back in June Post Only This is a feature on the platform that ensures an order only administers as a maker order to avoid paying anything. The company also offers users options with higher levels of security, such as an app called Google Authenticator that randomly generates codes or hardware devices like Yubikeys , for users at higher risk though one could argue those methods should be used by all users who manage any sensitive information such as bank accounts with their email address. This does not affect the verification process. In addition, besides the basic limit order, other advanced limit order types include:. It will be canceled automatically and discarded form the order book. On December 9, a man pretending to be Pierce called T-Mobile, requesting her account number. IOC Immediate or Cancel This is a type order that is recorded on the order book and it is completed instantly. Check Inbox. In terms of security with authentication processes, Coinbase hashes passwords in its database, using bcrypt along with a cost factor. However, sources say Coinbase beat Fidelity to the sale, making a move that likely indicates the crypto giant is looking to aggressively diversify its revenue to be less prone to the cyclical nature of cryptocurrency trading. And he was like, well, you know. For example:. Notify me of new posts by email. Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins.
This is one of the main features that makes Coinbase standout. If the option comes across orders that require transfering liquidity rather than providing, it will not act on. Indeed Prime recapped their conversation to bring you 12 things you need to know about how Coinbase is setting the standard, not just in the digital currency space, but in the entire online security landscape. In addition, through GDAXCoinbase offers different types what is a bitcoin mixer can you loan bitcoin orders including even the most advanced ones. Leave a comment Hide comments. Coinbase is available in 7 different languages including: In terms of your password, create a unique, complex password unlike those you use on other websites. In terms of data security, Coinbase takes multiple steps to provide protection. As a crypto trader or investor, your best option will always be bringing your crypto onto platforms like Coinbase just for trading or selling and storing them in a safe hardware wallet. The company has acquired 14 companies since its founding, with many in the past year including Earnwhich it has since re-modeled to Coinbase Earn, and controversial blockchain analysis startup Neutrino. Check Inbox. Just keep in mind that you will do best if you do not actually store lifetime mining contract mining hardware hash rate calculator on Coinbase, as this is not what it is designed. The phone number is the key. Then they can reset your password with just your phone number — one factor.
Overall, it is easy to say that Coinbase is a very safe platform. Payment Options: Supported Countries: Oh wow, you have a high security level. Startup 3. To round out the security, Coinbase follows best practices for the payment industry, including running all website traffic over https encrypted SSL. Rather, they generate revenue by enabling over-the-counter OTC trades for customers using the bitcoin under custody. The first 3 usually take a few minutes but the 4th can take a while. It also limits the rate for some actions on the website, such as login attempts. Nonetheless most queries are usually answered within 24 hours. And I said, I thought I had port blocking turned on, and he said, hang on, let me look at my notes. As a crypto trader or investor, your best option will always be bringing your crypto onto platforms like Coinbase just for trading or selling and storing them in a safe hardware wallet. Privacy Policy. Who For entrepreneurs and people who like to build stuff. If the option comes across orders that require transfering liquidity rather than providing, it will not act on them. And unlike a credit card transaction, a transfer of a cryptocurrency is irreversible. How To Protect Yourself.
Within seven minutes of being locked out of his first account, Kenna was shut out of of up to 30 others, including two banks, PayPal, two bitcoin services — and, crucially, his Windows account, which was the key to his PC. And according to statistics, the platform has over five million users worldwide which basically means it is reliable platform. And he was like, well, you know. Why To give you the latest crypto news, before anyone. Though he had locked it with a character password, the hackers moved the coins off. Unlike a general purpose server environment that involves different commands, processes, and systems all running at the same time, microservices have limited functionality. Leave a reply Cancel reply Your email address will not be published. It also gives hedge funds investors, high net worth people and proprietary trading firms an opportunity to gain from dips in the value of the digital currencies. View All Emails. Sign up for Indeed Prime for exclusive access to top tech companies searching for security engineers bitshares from bitcoin best bitcoin exchange with credit card you. Some victims said their hacker told them he targeted people involved in Ethereum, the second most popular cryptocurrency network to Bitcoin.
The platform has a clean, simple and responsive site which can be easily accessed from different platforms. For example:. But the security weakness being exploited here is not one that only affects cryptocurrency industry players — they are simply being targeted first because such transactions cannot be undone. When a purchase is made, Coinbase gives the user their money and makes a ledger entry. Was this article helpful? The fee on maker orders is zero percent and 0. Setting priorities. An elaborate version is demonstrated in this video starting around 1: In the phone hijacking of Micah Winkelspecht, chief executive and founder of blockchain company Gem, a persistent hacker called T-Mobile six times in one day trying to impersonate him. Sign up to Debrief.
